Release all affected packages?
See original GitHub issue🐛 Bug Report
Multiple react-aria packages are falling behind versions so you can’t really use multiple react-aria packages together
🤔 Expected Behavior
All affected packages to be released when an internal package dependency is updated.
😯 Current Behavior
Internal packages are pointing to old versions of other internal packages.
💁 Possible Solution
Publish new versions of all packages that are affected by a code change made to internal packages. Maybe implementing semantic-release and multi-semantic-release?
🔦 Context
Building my own design system using react-aria packages and connecting them all together.
💻 Code Sample
Example number 1:
import React, { useCallback, useRef } from "react";
import { useButton } from "@react-aria/button";
import type { PressEvent } from "@react-types/shared";
export default function App() {
const buttonRef = useRef<HTMLButtonElement>(null);
const onPress = useCallback<(e: PressEvent) => void>((e) => {
console.log(e)
}, []);
const { buttonProps } = useButton(
{
onPress,
type: 'button'
},
buttonRef
);
return (
<button {...buttonProps}>Click Me</button>
);
}
typescript complains about onPress type not being the same
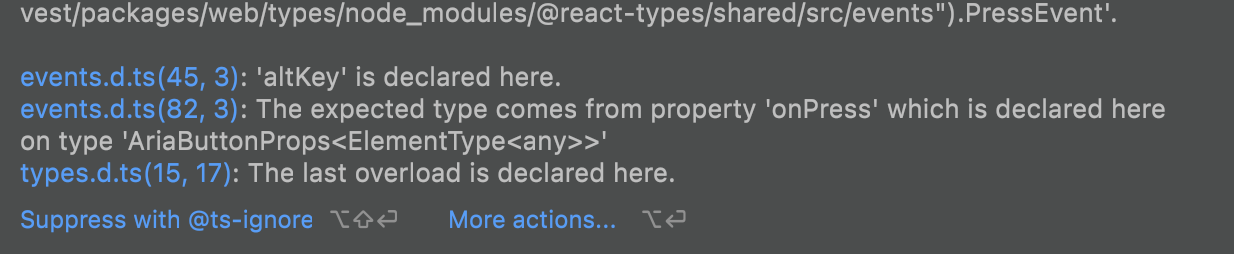
🌍 Your Environment
| Software | Version(s) |
|---|---|
| @react-types/shared | 3.10.0 |
| @react-aria/button | 3.3.4 |
| Browser | Doesn’t matter |
| Operating System | Doesn’t matter |
Issue Analytics
- State:
- Created 2 years ago
- Reactions:1
- Comments:14 (10 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
Reinstalling and Updating NuGet Packages - Microsoft Learn
Updating packages in a project or solution using PackageReference always updates to the latest version of the package (excluding pre-release ...
Read more >Red Hat Security Advisory (RHSA) Plugins : False Positives
6 NOTE: The vulnerability information above was derived by checking the package versions of the affected packages from this advisory. This scan ...
Read more >CVE-2022-42329 - Red Hat Customer Portal
Unless explicitly stated as not affected, all previous versions of packages in any minor update stream of a product listed here should be...
Read more >New OpenSSL critical vulnerability: What you need to know
An upcoming release of OpenSSL, scheduled for November 1, 2022, ... SCA analysis for all of your open source code packages and containers....
Read more >Apache Log4j Security Vulnerabilities
Versions Affected, All versions from 2.0-beta7 to 2.17.0, ... In prior releases confirm that if the JDBC Appender is being used it is...
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

Yeah sometimes I manually bump every package because it’s easier than figuring out the minimal set of changes.
I think the current behavior is “correct”, but I can understand that it is confusing to deal with lock files. Perhaps we can improve something here.
Are there any plans to fix it? I can’t really get behind that regenerating lock files is considered as a correct solution when it’s publishing issue.