401 JWT Token not found
See original GitHub issueHello everyone, I need a help. I will be very happy if someone helps me, because I am already on my second day over this problem. Thanks a lot.
I provided two versions of the security.yaml file. The second version according to API Platform documentation. API Platform sends to the creation a custom user provider. For the second option security.yaml recommended at API Platform docs, need to create two additional files, I did not attach them to the topic, but if necessary, attach.
But I think that problem it is in JWT.
Environment:
- node v8.9.4
- chrome 64.0.3282.119
- Ubuntu 16.04
- axios version: 0.16.2
- Vue.js 2.4.2
- vue-axios 2.0.2
- api-platform/api-pack: 1.0
- Symfony 4.0.4
User.php
<?php
namespace App\Entity;
use Doctrine\ORM\Mapping as ORM;
use Symfony\Component\Security\Core\User\UserInterface;
/**
* @ORM\Table(name="app_users")
* @ORM\Entity(repositoryClass="App\Repository\UserRepository")
*/
class User implements UserInterface, \Serializable
{
/**
* @ORM\Column(type="integer")
* @ORM\Id
* @ORM\GeneratedValue(strategy="AUTO")
*/
private $id;
/**
* @ORM\Column(type="string", length=25, unique=true)
*/
private $username;
/**
* @ORM\Column(type="string", length=64)
*/
private $password;
/**
* @ORM\Column(type="string", length=60, unique=true)
*/
private $email;
/**
* @ORM\Column(name="is_active", type="boolean")
*/
private $isActive;
public function __construct() // add $username
{
$this->isActive = true;
}
public function getUsername()
{
return $this->username;
}
public function getSalt()
{
// you *may* need a real salt depending on your encoder
// see section on salt below
return null;
}
public function getPassword()
{
return $this->password;
}
public function getRoles()
{
return array('ROLE_ADMIN');
}
public function eraseCredentials()
{
}
/** @see \Serializable::serialize() */
public function serialize()
{
return serialize(array(
$this->id,
$this->username,
$this->password,
// see section on salt below
// $this->salt,
));
}
/** @see \Serializable::unserialize() */
public function unserialize($serialized)
{
list (
$this->id,
$this->username,
$this->password,
// see section on salt below
// $this->salt
) = unserialize($serialized);
}
}
First option security.yaml
security:
encoders:
App\Entity\User:
algorithm: bcrypt
providers:
our_db_provider:
entity:
class: App\Entity\User
property: username
firewalls:
dev:
pattern: ^/(_(profiler|wdt)|css|images|js)/
security: false
login:
pattern: ^/api/login
stateless: true
anonymous: true
form_login:
check_path: /api/login_check
success_handler: lexik_jwt_authentication.handler.authentication_success
failure_handler: lexik_jwt_authentication.handler.authentication_failure
require_previous_session: false
api:
pattern: ^/api
stateless: true
provider: our_db_provider
guard:
authenticators:
- lexik_jwt_authentication.jwt_token_authenticator
access_control:
- { path: ^/admin, roles: ROLE_ADMIN }
- { path: ^/api/login, roles: IS_AUTHENTICATED_ANONYMOUSLY }
- { path: ^/api, roles: IS_AUTHENTICATED_FULLY }
Second option security.yaml
security:
encoders:
App\Entity\User:
algorithm: bcrypt
App\Security\User\WebserviceUser: bcrypt
providers:
our_db_provider:
entity:
class: App\Entity\User
property: username
webservice:
id: App\Security\User\WebserviceUserProvider
firewalls:
dev:
pattern: ^/(_(profiler|wdt)|css|images|js)/
security: false
login:
pattern: ^/api/login
stateless: true
anonymous: true
provider: webservice
form_login:
check_path: /api/login_check
success_handler: lexik_jwt_authentication.handler.authentication_success
failure_handler: lexik_jwt_authentication.handler.authentication_failure
require_previous_session: false
api:
pattern: ^/api
stateless: true
provider: our_db_provider
guard:
authenticators:
- lexik_jwt_authentication.jwt_token_authenticator
access_control:
- { path: ^/admin, roles: ROLE_ADMIN }
- { path: ^/api/login, roles: IS_AUTHENTICATED_ANONYMOUSLY }
- { path: ^/api, roles: IS_AUTHENTICATED_FULLY }
Headers
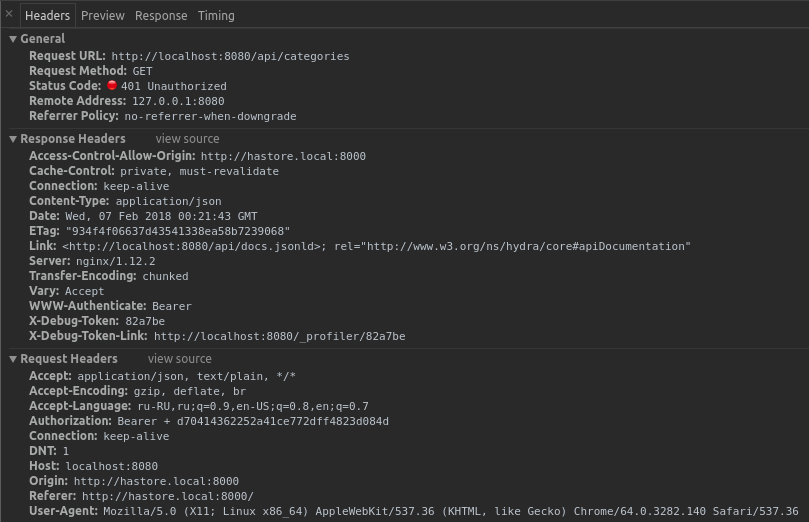
curl
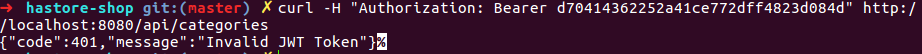
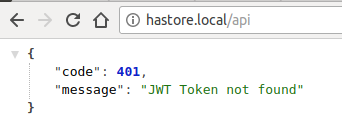
In browser
.env
###> lexik/jwt-authentication-bundle ###
# Key paths should be relative to the project directory
JWT_PRIVATE_KEY_PATH=var/jwt/private.pem
JWT_PUBLIC_KEY_PATH=var/jwt/public.pem
JWT_PASSPHRASE=d70414362252a41ce772dff4823d084d
###< lexik/jwt-authentication-bundle ###
lexik_jwt_authentication.yaml
lexik_jwt_authentication:
private_key_path: '%kernel.project_dir%/%env(JWT_PRIVATE_KEY_PATH)%'
public_key_path: '%kernel.project_dir%/%env(JWT_PUBLIC_KEY_PATH)%'
pass_phrase: '%env(JWT_PASSPHRASE)%'
Issue Analytics
- State:
- Created 6 years ago
- Comments:15 (5 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
401 JWT Token not found - Stack Overflow
My solutions was to add this in .htaccess RewriteCond %{HTTP:Authorization} ^(.*) RewriteRule .* - [e=HTTP_AUTHORIZATION:%1].
Read more >Getting the JWT Token Not Found Error, But Token Is In Header
I can get a token just fine: curl -X POST http://sandbox.localhost.com/login_check -d ... {"code":401,"message":"JWT Token not found"}.
Read more >JWT token not found" when invoking rest API to update DQ ...
This issue occurs because of using Authorization as basic authorization, and the token is not used. Solution.
Read more >401-Unauthorized developer token in Apple Music API
After creating the JWT developer token, when i try to access the API, An error of 401 - Unauthorized occurs. I am doing...
Read more >Troubleshooting issues with HTTP API JWT authorizers
The following provides troubleshooting advice for errors and issues that you might encounter when using JSON Web Token (JWT) authorizers with HTTP APIs....
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

Then I doing this instructions: https://techjourney.net/how-to-decrypt-an-enrypted-ssl-rsa-private-key-pem-key/ and get :
It’s looks like success. @chalasr, tell me please, if the private is decrypt via command line in manual, this is normal or I need decrypt via program code?
If be I did not use Postman, then I would not have seen the error of Symfony, which helped me find the root of the problem. It would be nice if be Lesik LexikJWTAuthenticationBundle processed this error.
Thanks a lot for help all who helped me.
@chalasr, thanks a lot. Yes, close issue.