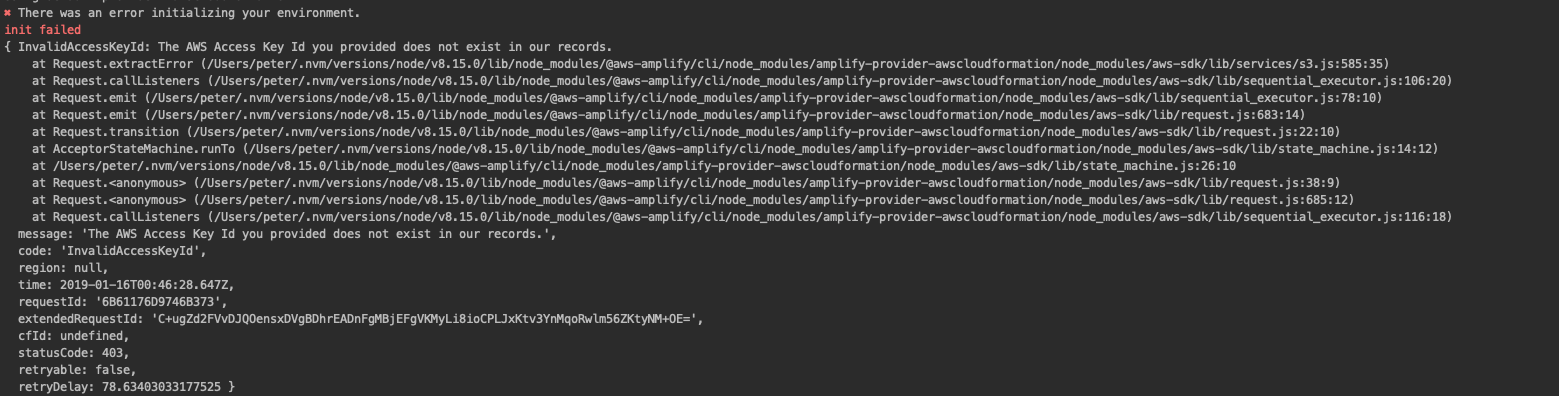
The AWS Access Key Id you provided does not exist in our records
See original GitHub issueDescribe the bug Receiving following invoking any operation
The AWS Access Key Id you provided does not exist in our records
To Reproduce Steps to reproduce the behavior:
- Using access key generated using STS - very definitely valid - was working previously via a named profile - correctly specified in config.
- Run any command e.g.
amplify initoramplify env pull
Expected behavior Should successfully authenticate and run expected operations.
Screenshots
If applicable, add screenshots to help explain your problem
Desktop (please complete the following information):
- OS: MacOS
- Browser N/A
- Version 0.2.1-multienv.26, also tried revert and run with 0.2.1-multienv.21
Issue Analytics
- State:
- Created 5 years ago
- Comments:9 (5 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
The AWS Access Key Id does not exist in our records
A client error (InvalidAccessKeyId) occurred when calling the ListBuckets operation: The AWS Access Key Id you provided does not exist in our records....
Read more >Why am I getting the "The AWS Access Key Id you ... - YouTube
Why am I getting the "The AWS Access Key Id you provided does not exist in our records ” error?
Read more >AWS Access Key Id you provided does not exist in our records
Hello, When doing the following step: $ aws s3 mb s3://<bucket-name> # Step 9. I am having the following error: "make_bucket failed: s3://testing.f1.cl...
Read more >The AWS Access Key Id does not exist in our records
The "AWS Access Key Id does not exist in our records" error occurs when the access key id configured for the AWS CLI...
Read more >"AWS Access Key ID you provided does not exist in ... - MSP360
The security credentials (secret and/or access keys) of your AWS IAM user have either expired, were made inactive in the AWS management console,...
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

Please also check my response to #709 Temp credentials directly got from STS would not directly work in the normal cli profile setup. Because as you guys have found out, the cli does not read session_token from the config file, and for temp credentials, the api call will fail without the session_token.
It’s an interesting decision not to support this? In a lot of large enterprises (including some major customers), I’m aware that STS sign in is the only option available for such operations as in these situations devs can’t get any other programmatic access to AWS via any other mechanism?
Personally I’m of the opinion that the auth mechanisms supported by other AWS tools (Node SDK) should be supported here… It was working fine for me up to recently?