Federated with Auth0 - Invalid login token. Issuer doesn't match providerName
See original GitHub issueBefore opening, please confirm:
- I have searched for duplicate or closed issues and discussions.
- I have read the guide for submitting bug reports.
- I have done my best to include a minimal, self-contained set of instructions for consistently reproducing the issue.
JavaScript Framework
React Native
Amplify APIs
Authentication
Amplify Categories
auth
Environment information
# Put output below this line
Describe the bug
Unable to federated with Auth0 after following all the Amplify doc. Error: Invalid login token. Issuer doesn’t match providerName.
Expected behavior
Successful federation, like described in the doc: https://docs.amplify.aws/lib/auth/advanced/q/platform/js/#federate-with-auth0
Reproduction steps
- Follow all the setup from the doc (https://docs.amplify.aws/lib/auth/advanced/q/platform/js/#federate-with-auth0)
- including, OpenID connect setup at IAM and Identity Pool
- fetch an idToken from Auth0
- Decode the token for iss (which is the issuer of the token - the domain), and exp (expiration)
- Federated Login using Amplify Auth
- domain equals iss (https://mydomain.auth0.com/)
- token equals to jwt idToken from Auth0 (checked signature and iss equals to domain using jwt.io)
- expires_at equals to idTokenPayload.exp
Code Snippet
Auth.federatedSignIn(
idTokenPayload.iss, // https://mydomain.auth0.com/
{
token: response.idToken,
expires_at: idTokenPayload.exp * 1000,
},
{
email: idTokenPayload.email,
},
)
Log output
Error: Invalid login token. Issuer doesn't match providerName.
aws-exports.js
Amplify.configure({
Auth: {
identityPoolId: xxx,
region: xxx,
identityPoolRegion: xxx,
mandatorySignIn: false,
},
})
Manual configuration
No response
Additional configuration
No response
Mobile Device
No response
Mobile Operating System
Android 11
Mobile Browser
No response
Mobile Browser Version
No response
Additional information and screenshots
No response
Issue Analytics
- State:
- Created 2 years ago
- Comments:9 (4 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
AWS Cognito getId "Invalid login token. Issuer doesn't match ...
so it exactly matches what the token has in the iss field, but that does not solve the problem, still the same message...
Read more >Troubleshoot SAML Configurations - Auth0
This error occurs when the InResponseTo attribute in the SAML response is not recognized by the Auth0 tenant. This error could be caused...
Read more >AWS-Amplify/Lobby - Gitter
I'm trying to get Amplify + Cognito + Federated Office 365 / Azure AD login working. Currently stuck with "Invalid login token. Issuer...
Read more >Adding OIDC identity providers to a user pool - Amazon Cognito
This feature is independent of federation through Amazon Cognito identity ... Amazon Cognito doesn't support client_secret_basic client authentication.
Read more >Invalid Login Token - LoginsLink
Invalid login token. Issuer doesn't match providerName - Giters. https://giters.com/aws-amplify/amplify-js/issues/9315.
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

Ahh, yeah that is an easy thing to miss. I’ll mention it to the Cognito team and link them to this issue. Thank you for pointing that out!
@chrisbonifacio Really appreciated on reminding me to re-visit the IAM identity provider. I figured out the root cause and need your help to report to the AWS console team. ( yeah i know it’s not the amplify team, thanks for the help! ) The issue is with the Provider URL field ( I inputted the trailing slash that causes the problem, but the cognito idpool console does not show the trailing slash after the auto-link from IAM)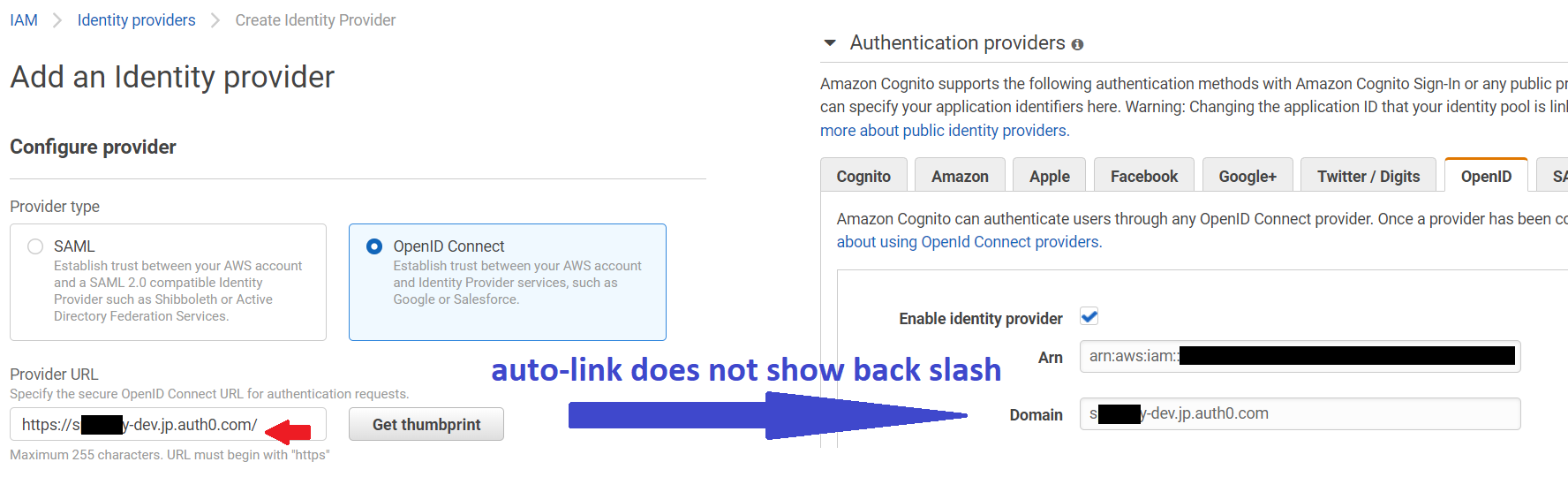
The ticket can be closed now. Thanks again and highly appreciated! Spent two days on this issue~