How to track Cognito events automatically through Pinpoint.
See original GitHub issueBefore opening, please confirm:
- I have searched for duplicate or closed issues and discussions.
- I have read the guide for submitting bug reports.
- I have done my best to include a minimal, self-contained set of instructions for consistently reproducing the issue.
JavaScript Framework
React
Amplify APIs
Authentication, Analytics
Amplify Categories
auth, analytics
Environment information
System:
OS: Linux 5.14 Fedora 34 (KDE Plasma)
CPU: (12) x64 Intel(R) Core(TM) i7-8750H CPU @ 2.20GHz
Memory: 1.46 GB / 15.29 GB
Container: Yes
Shell: 5.8 - /usr/bin/zsh
Binaries:
Node: 14.18.1 - /usr/bin/node
npm: 6.14.15 - /usr/bin/npm
Browsers:
Firefox: 93.0
npmGlobalPackages:
@aws-amplify/cli: 5.3.1
@microsoft/rush: 5.50.0
@openscreen/sdk: 0.3.0
aws-cdk: 1.118.0
aws-sdk: 2.968.0
eslint: 7.32.0
pnpm: 6.7.1
typescript: 4.3.5
The only package that is related to the issue is aws-amplify. The issue is captured on several 3.x.x and 4.x.x versions, incl. the latest one.
Describe the bug
Trying to have Cognito events (signups and signins) + session starts/ends appear in Pinpoint console. After creating a Congito User Pool and Pinpoint project outside Amplify (without using CLI) and putting them into Amplify.configure({...}) no events are being recorded.
The only indication of the issue is a console message on the web app itself. See Log Output below.
Expected behavior
Auth usage (signIn, signUp, etc) as well as session starts being recorded by Pinpoint and are visible in Pinpoint Console.
Reproduction steps
Prerequisites are a Pinpoint project and Cognito User Pool
CDK, but doable through web console
// see '@aws-cdk/aws-pinpoint'
const app = new CfnApp(this, 'PinpointApp', {
name: 'PinpointApp',
})
// cfnUserPoolClient instance of CfnUserPoolClient class in '@aws-cdk/aws-cognito'
cfnUserPoolClient.analyticsConfiguration = {
applicationArn: app.attrArn
userDataShared: true,
}
The steps are:
- Install
aws-amplify. - Amplify is configured with Auth and Analytics categories as per Amplify docs. See code snippet below
Code Snippet
Amplify.configure({
Auth: {
region: 'xxx',
userPoolId: 'xxx',
userPoolWebClientId: 'xxx'
},
Analytics: {
disabled: false,
autoSessionRecord: true,
AWSPinpoint: {
appId: 'xxx',
region: 'xxx'
},
}
})
Log output
Uncaught (in promise) Error: No credentials, applicationId or region
at AWSPinpointProvider.eval (AWSPinpointProvider.js:176)
at step (AWSPinpointProvider.js:55)
at Object.eval [as next] (AWSPinpointProvider.js:36)
at fulfilled (AWSPinpointProvider.js:27)
Manual configuration
const awsmobile = {
Auth: {
region: 'xxx',
userPoolId: 'xxx',
userPoolWebClientId: 'xxx'
},
Analytics: {
disabled: false,
autoSessionRecord: true,
AWSPinpoint: {
appId: 'xxx',
region: 'xxx'
},
}
}
Additional information
After going through 4-5 similar issues, I’ve tried multiple solutions, none of which have worked. In most of them it appears that people who got their issue resolved had it due to mismatching package versions or duplicates, which isn’t the case for me.
Attaching mandatorySignIn: false to Auth category for .configure({...}) as per similar closed issues didn’t work.
Issue Analytics
- State:
- Created 2 years ago
- Comments:8 (6 by maintainers)

 Top Related StackOverflow Question
Top Related StackOverflow Question
Oh okay, I think I understand your use case. You’ll still need to have an identity pool ID if using the Amplify Analytics library to record any events.
However, based off your use case, you can enable Cognito analytics in the console by navigating to your User Pool -> Analytics -> select an App Client and Pinpoint project.
You will need to adjust the IAM role permissions for the Auth Role of your Identity Pool. I configured mine like so but you can limit the
mobileanalyticsandmobiletargetingactions to just the Pinpoint project’s ARN:Also, edit the Identity Pool and set the Cognito Authentication Provider to your User Pool and App Client IDs.
Afterwards, I can see that my app is automatically recording auth events and sending them to Pinpoint.
Sign Up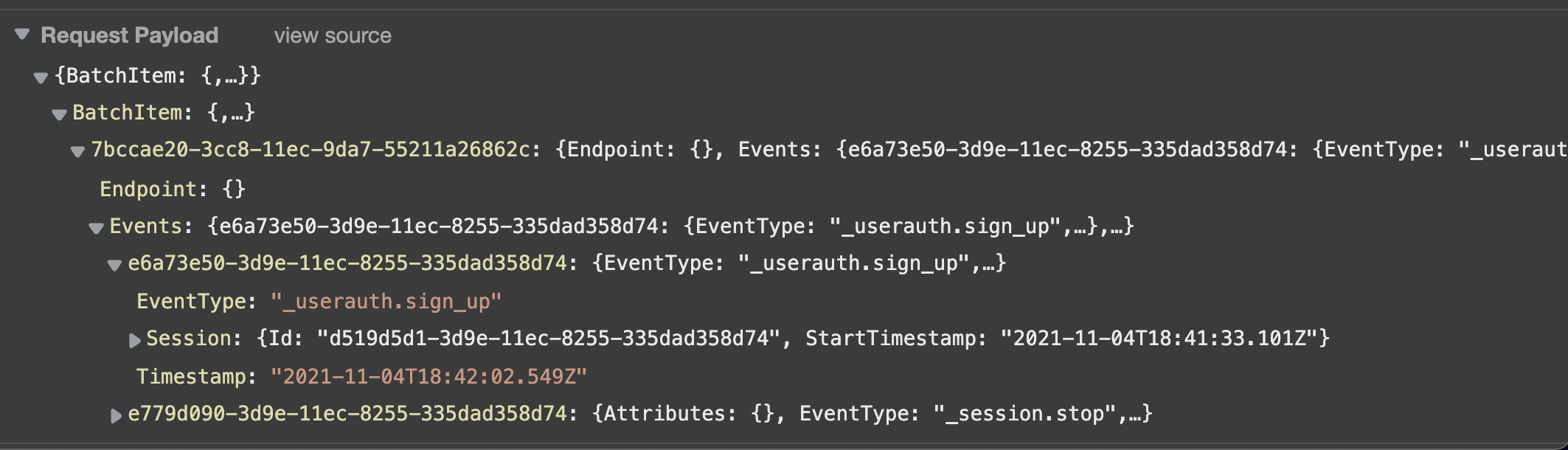
Sign In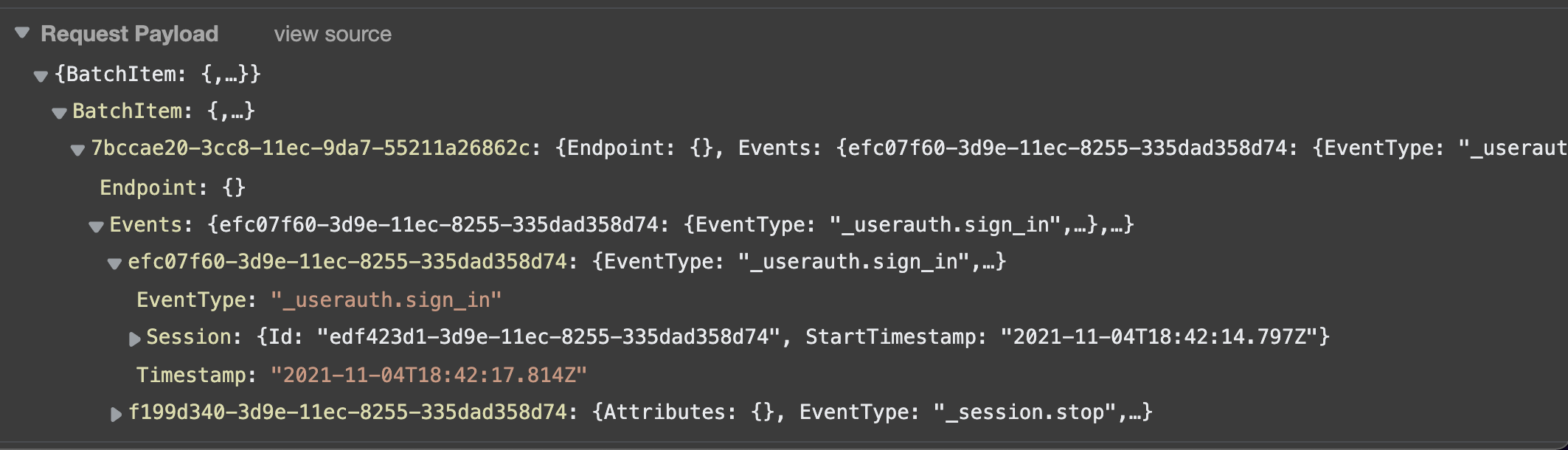
Sign Out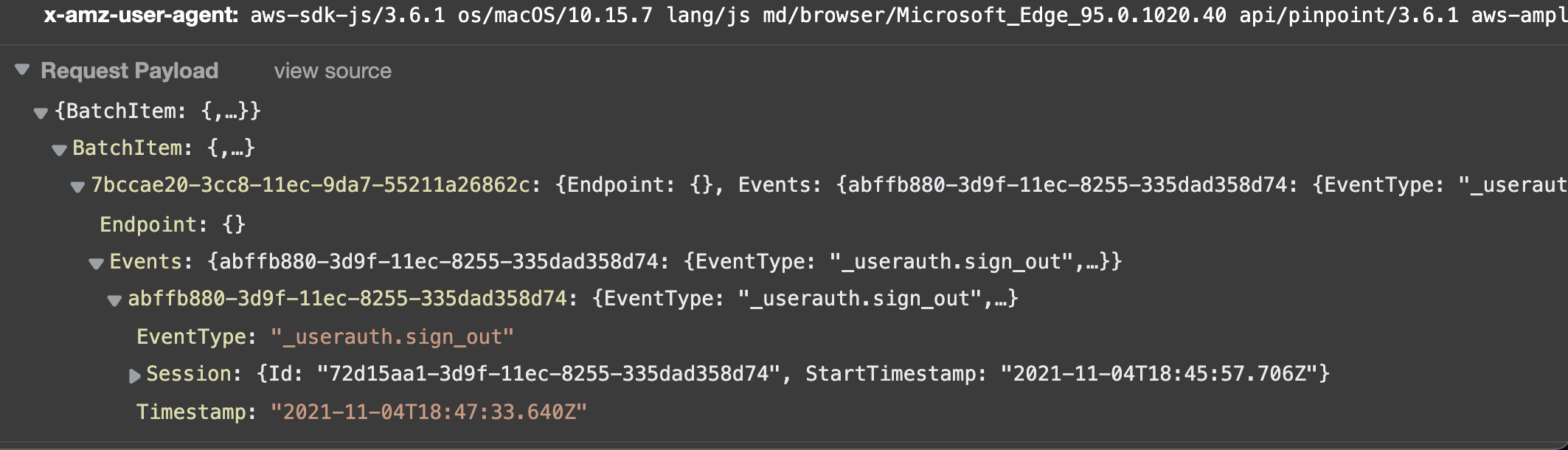
If you’re curious, this is how I was able to see that you needed to configure an Identity Pool by using the Amplify Debug Logger.
index.js
Output with no
identityPoolIdproperty in Auth config