NotAuthorizedException: Token is not from a supported provider of this identity pool.
See original GitHub issueDescribe the bug
Unable to login with Facebook (react-native).
To Reproduce
- Run through the default social provider auth flow with
amplify add auth - Create a facebook app, add appId + appSecret to amplify config
- Add app domain provided by cognito to FB dev page
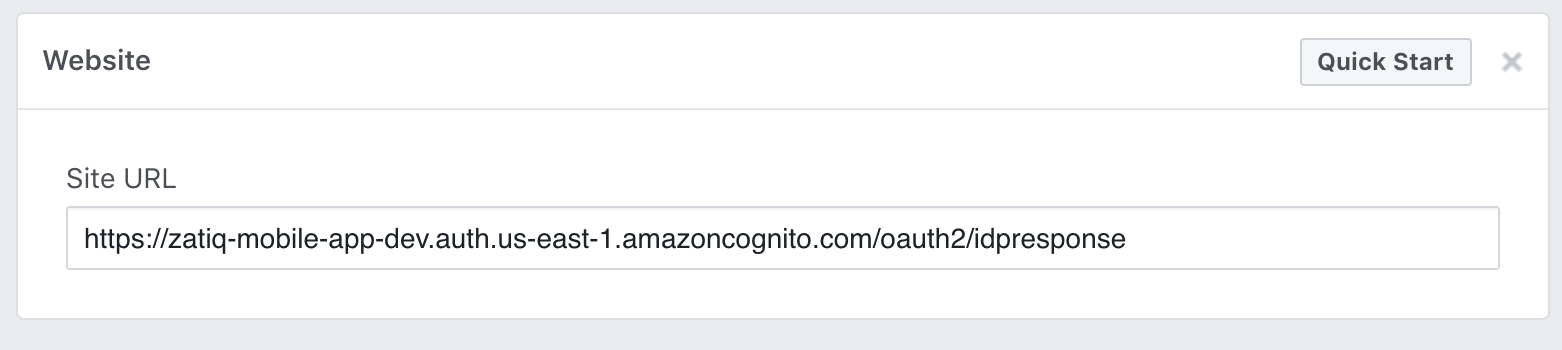
- Set the website with appended path (eg: https://zatiq-mobile-app-dev.auth.us-east-1.amazoncognito.com/oauth2/idpresponse)
- Use the example code for setting up react native facebook login (PS Expo no longer exposes a facebook property, it now comes from ‘expo-facebook’ package).
- Attempt to sign with
Auth.federatedSignIn
results in: NotAuthorizedException: Token is not from a supported provider of this identity pool.
Expected behavior Should receive credentials
Screenshots && Full Code Samples Here they are, I hope they help:
Generated aws-exports.js file (imported at the root of the app):
const awsmobile = { "aws_project_region": "us-east-1", "aws_cognito_identity_pool_id": "us-east-1:b34dbc6d-dd57-4bd8-9e00-10d8e47039ea", "aws_cognito_region": "us-east-1", "aws_user_pools_id": "us-east-1_SYQGQiN5S", "aws_user_pools_web_client_id": "t851knsevlqsm11spa7huoerj", "oauth": { "domain": "zatiq-mobile-app-dev.auth.us-east-1.amazoncognito.com", "scope": [ "phone", "email", "openid", "profile", "aws.cognito.signin.user.admin" ], "redirectSignIn": "exp://192.168.2.15:19000/", "redirectSignOut": "exp://192.168.2.15:19000/", "responseType": "code" }, "federationTarget": "COGNITO_USER_POOLS", "aws_content_delivery_bucket": "zatiq-mobile-app-hosting-dev", "aws_content_delivery_bucket_region": "us-east-1", "aws_content_delivery_url": "http://zatiq-mobile-app-hosting-dev.s3-website-us-east-1.amazonaws.com" };
Cognito config verifying Facebook data is there (I have omitted the app secret for this screenshot)
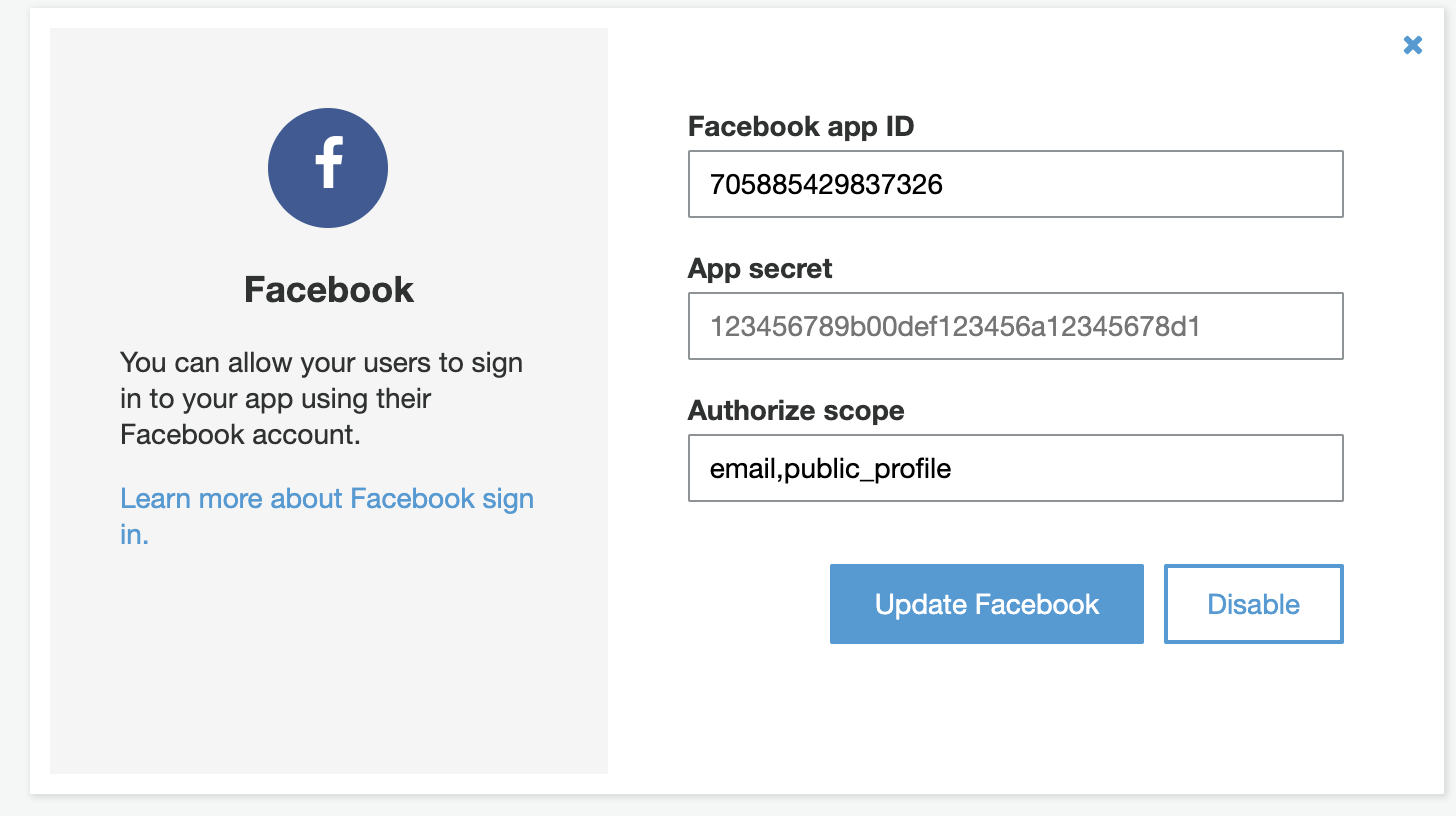
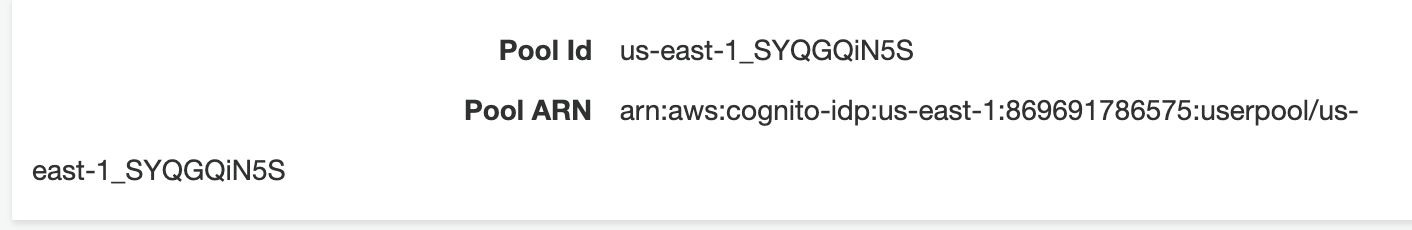
Verifying that I haven’t used the wrong cognito pool:
Screenshot of setting the website url on facebook with appended paths:
full login code:
`const signIn = async () => { const { type, token, expires } = await Facebook.logInWithReadPermissionsAsync( ‘705885429837326’, { permissions: [‘public_profile’], behavior: ‘native’, } );
if (type === 'success') {
const response = await fetch(`https://graph.facebook.com/me?access_token=${token}`);
const { name } = await response.json();
Auth.federatedSignIn(
'facebook',
{ token, expires_at: expires },
{ name, }
)
.then(credentials => {
console.log('get aws credentials', credentials);
}).catch(e => {
console.log(e);
});
}
}`
Desktop (please complete the following information):
- OS: macOS Mojave
- Browser Chrome
Smartphone (please complete the following information):
- Device: [e.g. iPhone6]
- OS: [e.g. iOS8.1]
- Browser [e.g. stock browser, safari]
- Version [e.g. 22]
I’ve checked other issues in this repo (there are a few that have this same error) but alas was unable to pinpoint what I’m doing wrong 😦
Issue Analytics
- State:
- Created 4 years ago
- Reactions:4
- Comments:14 (4 by maintainers)

 Top Related StackOverflow Question
Top Related StackOverflow Question
The issue was actual for me as well. Identity poll was created but I have to put manually Facebook App Id and Google App Id to Authentication providers list
@Jun711 it didn’t work without Federated Identities pool Authentication providers for me in January. Without Federated Identities pool Authentication providers Amplify CLI didn’t push tokens to the AWS Cognito however, they were configured locally in the CLI.
There is a chance that it was fixed with new releases, but I didn’t check