User session is not refreshed after period of idle in the browser
See original GitHub issueDescribe the bug
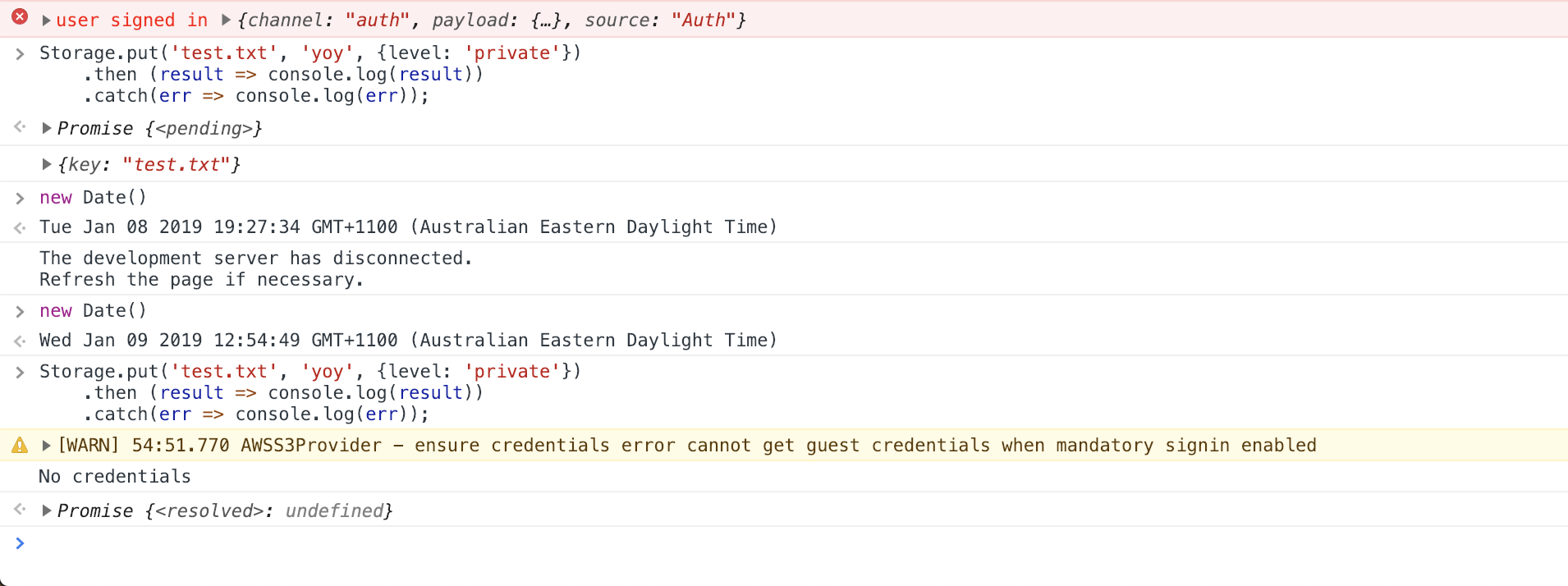
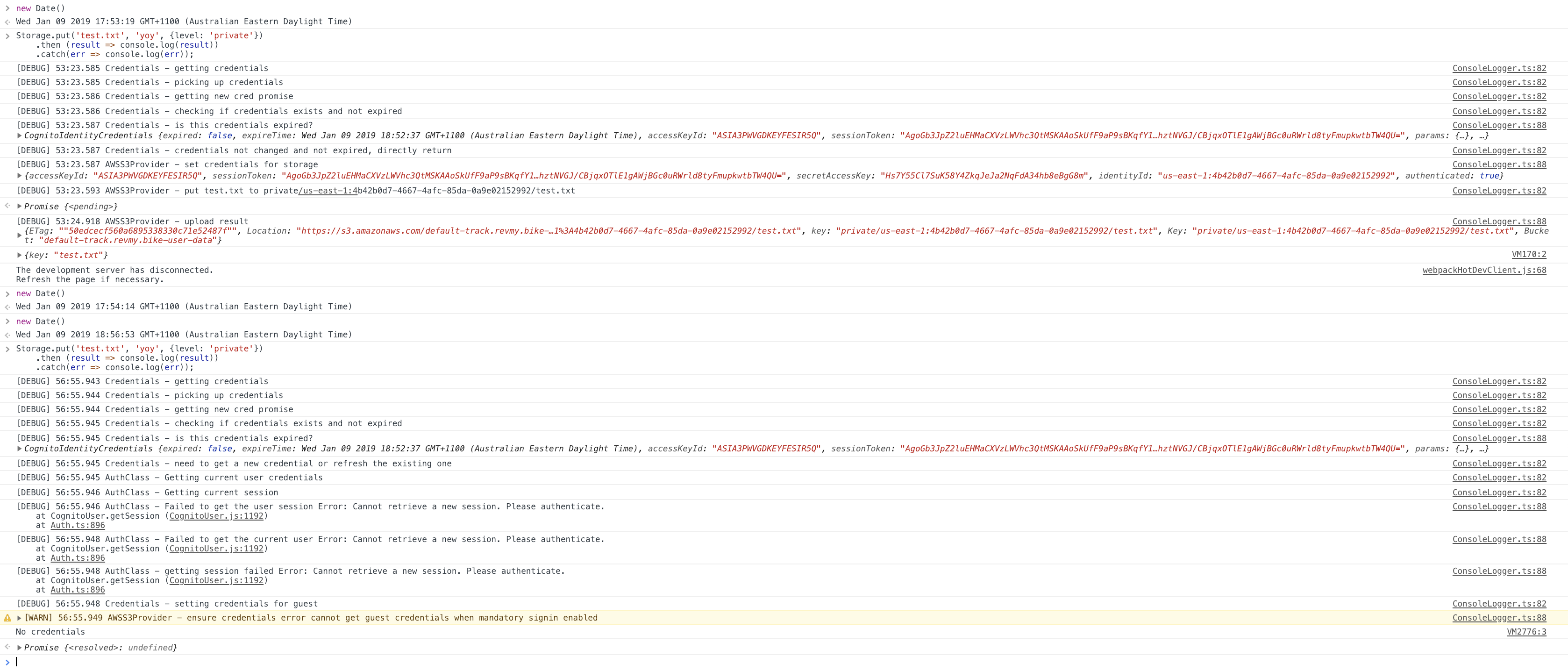
Getting No credentials (more - [WARN] 33:03.724 AWSS3Provider - ensure credentials error cannot get guest credentials when mandatory signin enabled) after a period of inactivity.
To Reproduce Steps to reproduce the behaviour:
- Use the example code attached below.
- Sign In via hosted UI (redirect back to the site - localhost in my case).
- The current user is correctly read;
HubsignInnotification is correctly received. - Upload a file to S3 using
StorageAPI (-> successfully) - Wait for a while (in my case it was ~12hrs~ 1hr)
- Upload a file to S3 using
StorageAPI
Expected behaviour After step 6, I am expecting Amplify to automatically refresh the token and upload the file successfully.
But actual behaviour is that the current user is no longer available and as such upload fails.
Screenshots
Desktop (please complete the following information):
- OS: macOS 10.14
- Browser: Chrome 71
- Amplifyjs version: 1.1.18
Additional context
The JS code on the web page:
import Amplify, { Auth, Hub, Storage } from 'aws-amplify';
Amplify.configure({
Auth: {
identityPoolId: process.env.ELM_APP_IDENTITY_POOL_ID,
region: process.env.ELM_APP_REGION,
userPoolId: process.env.ELM_APP_USER_POOL_ID,
userPoolWebClientId: process.env.ELM_APP_USER_POOL_CLIENT_ID,
mandatorySignIn: true,
oauth: {
domain: process.env.ELM_APP_OAUTH_DOMAIN,
scope: ['phone', 'email', 'profile', 'aws.cognito.signin.user.admin', 'openid'],
redirectSignIn: process.env.ELM_APP_OAUTH_SIGNED_IN_URL,
redirectSignOut: process.env.ELM_APP_OAUTH_SIGNED_OUT_URL,
responseType: 'token',
options: {
AdvancedSecurityDataCollectionFlag: false
}
},
},
Storage: {
bucket: process.env.ELM_APP_USER_FILES_BUCKET,
region: process.env.ELM_APP_REGION
}
});
// TODO: Expose for debugging purposes to play in console
window.app = app;
window.Auth = Auth;
window.Storage = Storage;
Hub.listen('auth', {
onHubCapsule: (capsule) => {
switch (capsule.payload.event) {
case 'signIn':
console.error('user signed in', capsule);
readCurrenUser(capsule.payload.data);
break;
case 'signUp':
console.error('user signed up', capsule);
break;
case 'signOut':
console.error('user signed out', capsule);
readCurrenUser(null);
break;
case 'signIn_failure':
console.error('user sign in failed', capsule);
break;
case 'configured':
console.error('the Auth module is configured', capsule);
break;
}
}
});
function readCurrenUser(user) {
window.user = user;
if (user) {
// TODO: Verify user is authenticated before asking for attributes (otherwise promise fails)
Auth.userAttributes(user).then(attributes => {
const email = attributes.find(x => x.Name == 'email').Value;
// TODO: debugging
window.userAttributes = attributes;
});
} else {
app.ports.currentUserSet.send(null);
}
};
// Get out with Auth.signOut()
// Trigger current user auth
Auth.currentAuthenticatedUser().then(user => readCurrentuser(user));
Full console output with debugging
Issue Analytics
- State:
- Created 5 years ago
- Comments:6 (4 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
How to reload a page automatically after a given period of ...
You can use $interval method from angularJS function reloadPage() { var d = new Date(); var curTime = d.
Read more >Setting the idle session timeout - IBM
If a user leaves their session idle in a web browser for the specified length of time, the user is automatically logged out...
Read more >Microsoft 365 Idle session Timeout Policy Available
Users affected by the policy will see a notification that their session is about to expire about a minute before the period ends...
Read more >Session Timeout Issues - Salesforce Help
If a User session is not timing out, then the User's session is being kept alive with activity from an alternative source. This...
Read more >SSO must be invalidated after Session Timeout
When user clicks Refresh the session will be active. This means that the user is not idle and is aware that he/she needs...
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

@powerful23 thanks, switching to
codeand will update (UPDATE: yeah it does refresh with thecodeflow)I couldn’t find in the docs that it stated it only refreshes token for
coderesponse type/flow. Perhaps some clarification is required in the docs?But I’m pretty sure the refresh token was returned with the
tokenflow too? This is what Amplify stored in the browser local storage:This issue has been automatically locked since there hasn’t been any recent activity after it was closed. Please open a new issue for related bugs.
Looking for a help forum? We recommend joining the Amplify Community Discord server
*-helpchannels or Discussions for those types of questions.