[BlobTrigger] Identity based connection with serviceUri: fail to send message to poison queue
See original GitHub issueHi,
According to the documentation Azure Blob Storage Trigger for AF §Identity Based Connection we should be able to use serviceBusUri parameter suffix for a connection string next to the AzureWebJobsStorage parameter for “internal Queue usage”:
By default, the blob trigger uses Azure Queues internally. In the serviceUri form, the AzureWebJobsStorage connection is used. However, when specifying blobServiceUri, a queue service URI must also be provided with queueServiceUri.
In the situation the function execution doesn’t succeed, the message should be sent to a poison queue. But in this configuration: it fails. The function displays the following error:
Detailed error
[2021-12-22T22:03:34.655Z] An unhandled exception has occurred. Host is shutting down.
[2021-12-22T22:03:34.657Z] Azure.Storage.Queues: The resource doesn't support specified Http Verb.
RequestId:a92c710e-b01e-002c-637f-f7fb39000000
Time:2021-12-22T22:03:34.4303100Z
[2021-12-22T22:03:34.658Z] Status: 405 (The resource doesn't support specified Http Verb.)
[2021-12-22T22:03:34.659Z] ErrorCode: UnsupportedHttpVerb
[2021-12-22T22:03:34.660Z]
[2021-12-22T22:03:34.661Z] Content:
[2021-12-22T22:03:34.662Z] <?xml version="1.0" encoding="utf-8"?>
<Error><Code>UnsupportedHttpVerb</Code><Message>The resource doesn't support specified Http Verb.
RequestId:a92c710e-b01e-002c-637f-f7fb39000000
Time:2021-12-22T22:03:34.4303100Z</Message></Error>
[2021-12-22T22:03:34.663Z]
[2021-12-22T22:03:34.664Z] Headers:
[2021-12-22T22:03:34.665Z] Server: Windows-Azure-Blob/1.0,Microsoft-HTTPAPI/2.0
[2021-12-22T22:03:34.666Z] x-ms-error-code: UnsupportedHttpVerb
[2021-12-22T22:03:34.667Z] x-ms-request-id: a92c710e-b01e-002c-637f-f7fb39000000
[2021-12-22T22:03:34.668Z] x-ms-version: 2018-11-09
[2021-12-22T22:03:34.669Z] Date: Wed, 22 Dec 2021 22:03:33 GMT
[2021-12-22T22:03:34.670Z] Allow: REDACTED
[2021-12-22T22:03:34.671Z] Content-Length: 243
[2021-12-22T22:03:34.672Z] Content-Type: application/xml
[2021-12-22T22:03:34.673Z] .
After some investigations, we understood that, in that situation, the host is doing the call on the wrong domain. Instead of using the AzureWebJobsStorage connectionstring to connect to the service and write in the webjobs-blobtrigger-poison queue, it uses the serviceUri URL (and so fail because it targets the Blob service and not the Queue one).
We verified this thanks to the error message and moreover thanks to a Fiddler tracing:
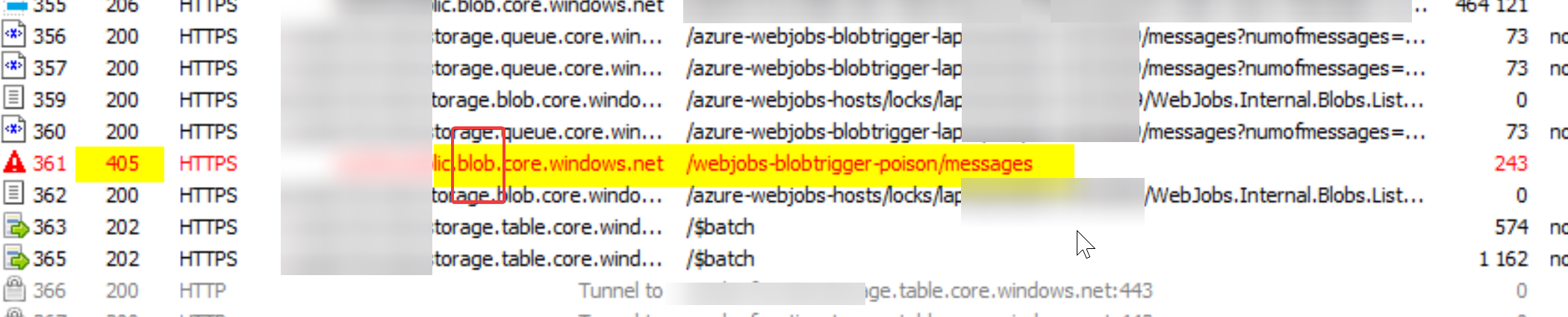
From our understanding of the documentation, it should rather get the Queue Client from the AzureWebJobsStorage connection string.
Investigative information
Please provide the following:
- Timestamp: 2021-12-22
- Function App version:
Azure Functions Core Tools Core Tools Version: 3.0.3904 Commit hash: c345f7140a8f968c5dbc621f8a8374d8e3234206 (64-bit) Function Runtime Version: 3.3.1.0 Aspnet Core 3.1
PackageReference Include="Microsoft.Azure.WebJobs.Extensions.Storage" Version="5.0.0" - Function App name: can be reproduced locally with Visual Studio Credentials
Repro steps
Create an Azure Function with the following Trigger:
public static async Task Run([BlobTrigger("my-container/{path}", Connection= "MyStorageConnection")]Stream fileStream, string path)
{
throw new Exception("Just make it fail");
}
Add to your user the right RBACs to the storage used for binding (Storage Blob Data Owner & Storage Queue Contributor).
Fill your loccal.settings.json as following:
{
"IsEncrypted": false,
"Values": {
"ASPNETCORE_ENVIRONMENT": "Debug",
"AzureWebJobsStorage": "FullConnectionStringToAStorageAcount",
"APPINSIGHTS_INSTRUMENTATIONKEY": "MY-APP-INSIGHT-KEY",
"MyStorageAccount__serviceUri": "https://<my-account-name>.blob.core.windows.net"
},
"ConnectionStrings": {
}
}
Run the function.
Put a file in the container my-container from the storage my-account-name
Expected behavior
A message should be sent to the poison queue and the function should continue to run.
Actual behavior
The message is not sent to the poison queue. The Function stops to run. The following error message is displayed:
[2021-12-22T22:03:34.655Z] An unhandled exception has occurred. Host is shutting down.
[2021-12-22T22:03:34.657Z] Azure.Storage.Queues: The resource doesn't support specified Http Verb.
RequestId:a92c710e-b01e-002c-637f-f7fb39000000
Time:2021-12-22T22:03:34.4303100Z
[2021-12-22T22:03:34.658Z] Status: 405 (The resource doesn't support specified Http Verb.)
[2021-12-22T22:03:34.659Z] ErrorCode: UnsupportedHttpVerb
[2021-12-22T22:03:34.660Z]
[2021-12-22T22:03:34.661Z] Content:
[2021-12-22T22:03:34.662Z] <?xml version="1.0" encoding="utf-8"?>
<Error><Code>UnsupportedHttpVerb</Code><Message>The resource doesn't support specified Http Verb.
RequestId:a92c710e-b01e-002c-637f-f7fb39000000
Time:2021-12-22T22:03:34.4303100Z</Message></Error>
[2021-12-22T22:03:34.663Z]
[2021-12-22T22:03:34.664Z] Headers:
[2021-12-22T22:03:34.665Z] Server: Windows-Azure-Blob/1.0,Microsoft-HTTPAPI/2.0
[2021-12-22T22:03:34.666Z] x-ms-error-code: UnsupportedHttpVerb
[2021-12-22T22:03:34.667Z] x-ms-request-id: a92c710e-b01e-002c-637f-f7fb39000000
[2021-12-22T22:03:34.668Z] x-ms-version: 2018-11-09
[2021-12-22T22:03:34.669Z] Date: Wed, 22 Dec 2021 22:03:33 GMT
[2021-12-22T22:03:34.670Z] Allow: REDACTED
[2021-12-22T22:03:34.671Z] Content-Length: 243
[2021-12-22T22:03:34.672Z] Content-Type: application/xml
[2021-12-22T22:03:34.673Z] .
Known workarounds
As a workaround for now, we use the “full config” with blobServiceUri and queueServiceUri and it works:
{
"IsEncrypted": false,
"Values": {
"ASPNETCORE_ENVIRONMENT": "Debug",
"AzureWebJobsStorage": "FullConnectionStringToAStorageAcount",
"APPINSIGHTS_INSTRUMENTATIONKEY": "MY-APP-INSIGHT-KEY",
"MyStorageAccount__blobServiceUri": "https://<my-account-name>.blob.core.windows.net",
"MyStorageAccount__queueServiceUri": "https://<my-account-name>.queue.core.windows.net",
},
"ConnectionStrings": {
}
}
Related information
Provide any related information
- Programming language used: C#
- Links to source: none
- Bindings used: BlobTrigger with User Managed Identity - Locally with Visual Studio Credentials
Thank you team 👏, let me know if you need more info
Issue Analytics
- State:
- Created 2 years ago
- Reactions:4
- Comments:7 (2 by maintainers)

 Top Related StackOverflow Question
Top Related StackOverflow Question
Hi @sescandell , Thank you for your feedback! We will investigate this further and update you with the findings.
cc @alrod