User cannot log out
See original GitHub issueI’m submitting a…
- Bug report
Browser:
- Chrome version XX
- Edge version 76.0.167.1
Library version
Library version: 1.0.1
Current behavior
- Use clicks logout. App uses MSAL logout() to redirect to:
https://login.microsoftonline.com/common/oauth2/v2.0/logout
?post_logout_redirect_uri=http://localhost:3000
Sometimes, AD stops at this page and asks the user to select which account they should log out of. Other times, it blows right past it and automatically redirects to the next page.
- Page redirects (on AAD/B2C side) to:
https://login.microsoftonline.com/common/oauth2/v2.0/logoutsession
Notice the post_logout_redirect_uri WAS in the first page, but is now gone. MSAL seems to be doing its part, but something gets lost during this redirect on the identity provider.
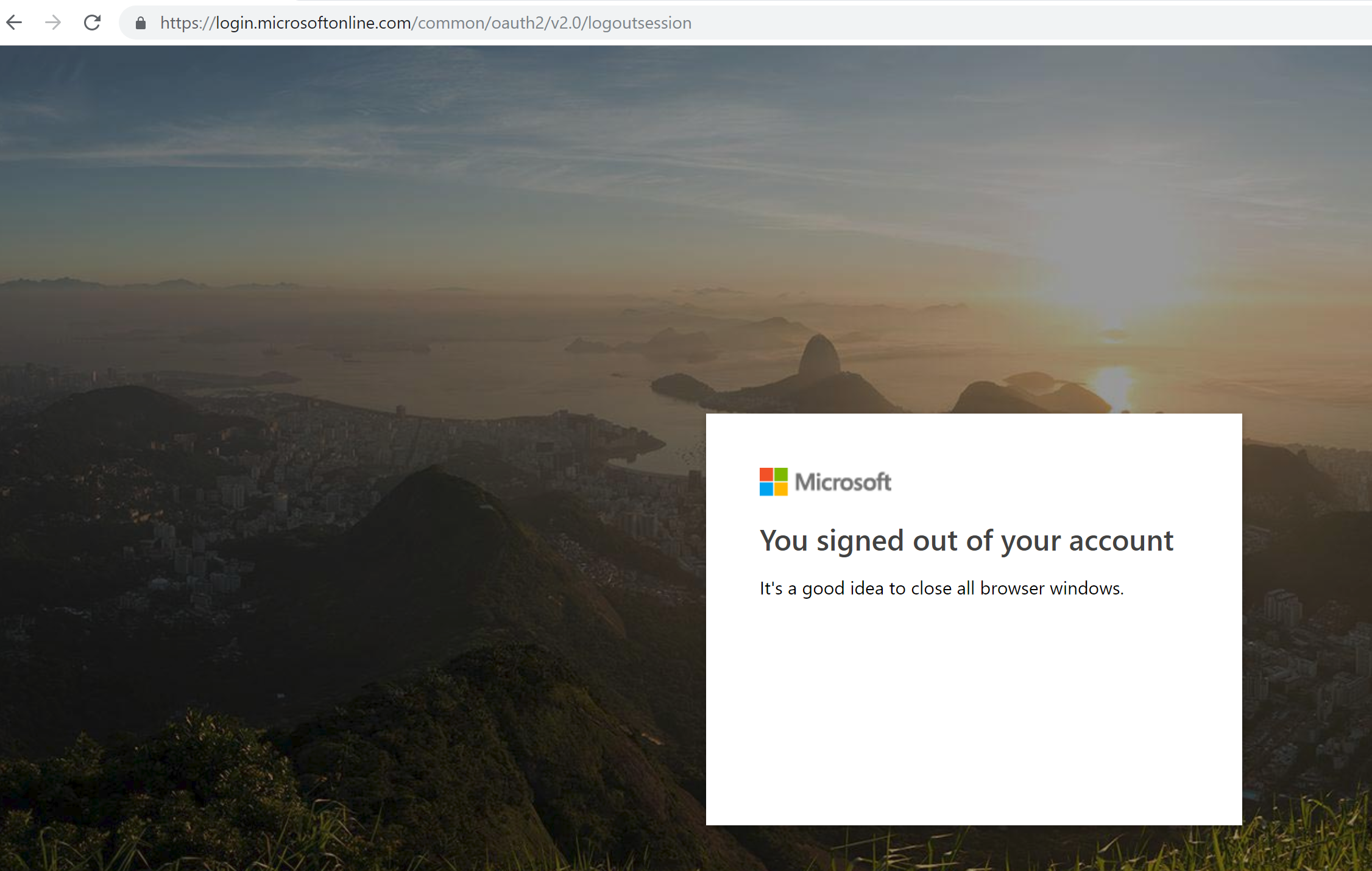
The page stays there with the message “You signed out of your account. It’s a good idea to close all browser windows”. The user has no way to return to the app.
-
Manually browse back to the app.
-
User does not appear to be logged in. A request is sent to:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize
?response_type=id_token%20token
&scope=profile openid offline_access user_impersonation
&client_id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX
&redirect_uri=http%3A%2F%2Flocalhost%3A3000
&state=d2820c44-3e2c-499b-8ebe-7e338c148413
&nonce=0e6504d0-0a8a-4c71-a06a-7143fee1cc58
&client_info=1&x-client-SKU=MSAL.JS
&x-client-Ver=1.0.0
&client-request-id=26def4cb-74bf-4211-8f39-15a4f13ca05f
&prompt=none
Which returns with the following from the hidden iFrame injected by MSAL: “Loading frame has timed out after: 6 seconds for scope profile openid offline_acces”
And the following from a manual call to MSAL acquireTokenSilent(): “Token renewal operation failed due to timeout.”
This is okay. I’d expect these to fail.
- User clicks login button. App calls MSAL loginRedirect(). Page redirects to:
https://login.microsoftonline.com/te/mytenant.onmicrosoft.com/b2c_1_signup-signin/oauth2/v2.0/authorize
?response_type=token
&scope=profile openid offline_access user_impersonation
&client_id=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX
&redirect_uri=http%3A%2F%2Flocalhost%3A3000
&state=8abd9bb6-605e-4ab3-8f61-0a1ff2e464a7
&nonce=35d90353-9a84-4099-90e2-2ce49a272994
&client_info=1&x-client-SKU=MSAL.JS
&x-client-Ver=1.0.0
&login_req=ba5c17b8-ad9a-4570-89b7-7edc88e11eb2-b2c_1_signup-signin
&domain_req=b39b039b-fe33-4653-8e63-7a7f59b3c864
&domain_hint=organizations
&client-request-id=cbe3310c-3ef5-460f-aae9-fa47973b5461
&prompt=none
User is NOT promped for credentials. They are authenticated and automatically redirected back to the app.
Expected behavior
- I expect the user to not have to select what account they want to log out of when they are only logged in with 1 account.
- I’d expect them to get redirected back to the app.
- I’d expect them to have to provide username and password after they appear to have been logged out in already.
Other
- I am working with Azure support on this as well, but so far they have seen nothing incorrectly configured on the B2C or Azure end. I decided to post it here in case there is something library related that will help.
- If the user closes and reopens the browser, they are fully logged out.
- Before clicking Login and skipping the credentials, there are no cookies or any info stored locally. I have no idea how it is bypassing the credential prompt.
Issue Analytics
- State:
- Created 4 years ago
- Comments:59 (23 by maintainers)

 Top Related StackOverflow Question
Top Related StackOverflow Question
For anyone who is stumped on this and finds this thread, I found a solution.
Similar to how you have to explicitly set your clientApplication authority before you redirect to login
this.clientApplication.authority = https://${msalTenant}.b2clogin.com/${msalTenant}.onmicrosoft.com/${msalSignInPolicy}; this.clientApplication.loginRedirect();You have to explicitly set this before triggering logout, otherwise you are directed to the common MS online logout page.
this.clientApplication.authority = https://${msalTenant}.b2clogin.com/${msalTenant}.onmicrosoft.com/${msalSignInPolicy}; this.clientApplication.logout();I figured this out by examining the network call to
openid-configurationwhen the login process is triggered. This comes back with an object that has the propertyend_session_endpointwhich matches the URL pattern above.In the source code for logout it looks for an end session endpoint and if it doesnt exist, redirects you to common login online for logout. Where your redirect URI is not configured and it breaks.
tldr; Set the client application authority before logging out. Set the logout redirect uri as a reply URL in your azure B2C application configuration.
I published the recorded steps so you can see:
https://youtu.be/XIiQZL7pERQ