Bug: Masking the password only if it is not the last key-value pair.
See original GitHub issueDescribe the bug TSLog masks password only if it is not the last value in the json.
To Reproduce Steps to reproduce the behavior:
mkdir tslogBugReplacecd tslogBugReplacenpm init -ynpm i tslog- Open directory with your favourite text editor and create index.js
- Run the following code:
const { Logger } = require('tslog');
let log = new Logger();
log.info({ password: 'topsecret', user: 'test'});
// password is masked.
log.info({ user: 'test', password: 'topsecret' });
// password is not masked!
log.info({ user: 'test', password: 'topsecret', iWillMask: 'Because I exist' });
// Whew! It's masked again.
// Hint: util.inspect() does not add a comma after the last key in json.
// In the following example:
// Keys do not include password.
// Only values have the keyword 'password' (case insensitive).
log.info({
errorCode: 'WrongPasswordOrEmail',
message: 'Email or Password is wrong! Password, password, password!',
anyKey: 'any value' // removing this key will result in unmasked message.
});
node index.jsor you can also see the screenshot below.
Expected behavior Password should be masked regardless of the comma at the end when it was serialized for replacement with the mask string.
Screenshots

Additional context I have seen the code for replacing the value of the key is using inspect from util library. A simple regex matching for every key-value pair is a bit hard to write. I am currently working on a depth first search approach, where each property is visited and modified then copied to a clone until a cycle is encountered. Finally I would call util.inpect() on the clone as well, and modify the result for pretty printing.
Issue Analytics
- State:
- Created 3 years ago
- Reactions:1
- Comments:5 (4 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
The Problem with Password Masking - Schneier on Security
I'm talking about password masking on personal computers. ... If you were to type it only once and not spot the error you...
Read more >Mask sensitive data in logs with logback - Stack Overflow
to uniformly mask for all calls (only logging). at the same time, but cannot. There is no way to mask two patterns in...
Read more >Masking Passwords · ActiveMQ Artemis Documentation
Set it to "true" if you want your passwords masked. The default value is "false". password-codec : this string type property identifies the...
Read more >6.4.1.2 Caching SHA-2 Pluggable Authentication
The server assigns the caching_sha2_password plugin to the account and uses it to encrypt the password using SHA-256, storing those values in the...
Read more >frequently_asked_questions [hashcat wiki]
When I run an attack with -a 3 and I do not specifying a mask, I see it working but what is it...
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

Well caught.
Another patch is on its way. Should look like this: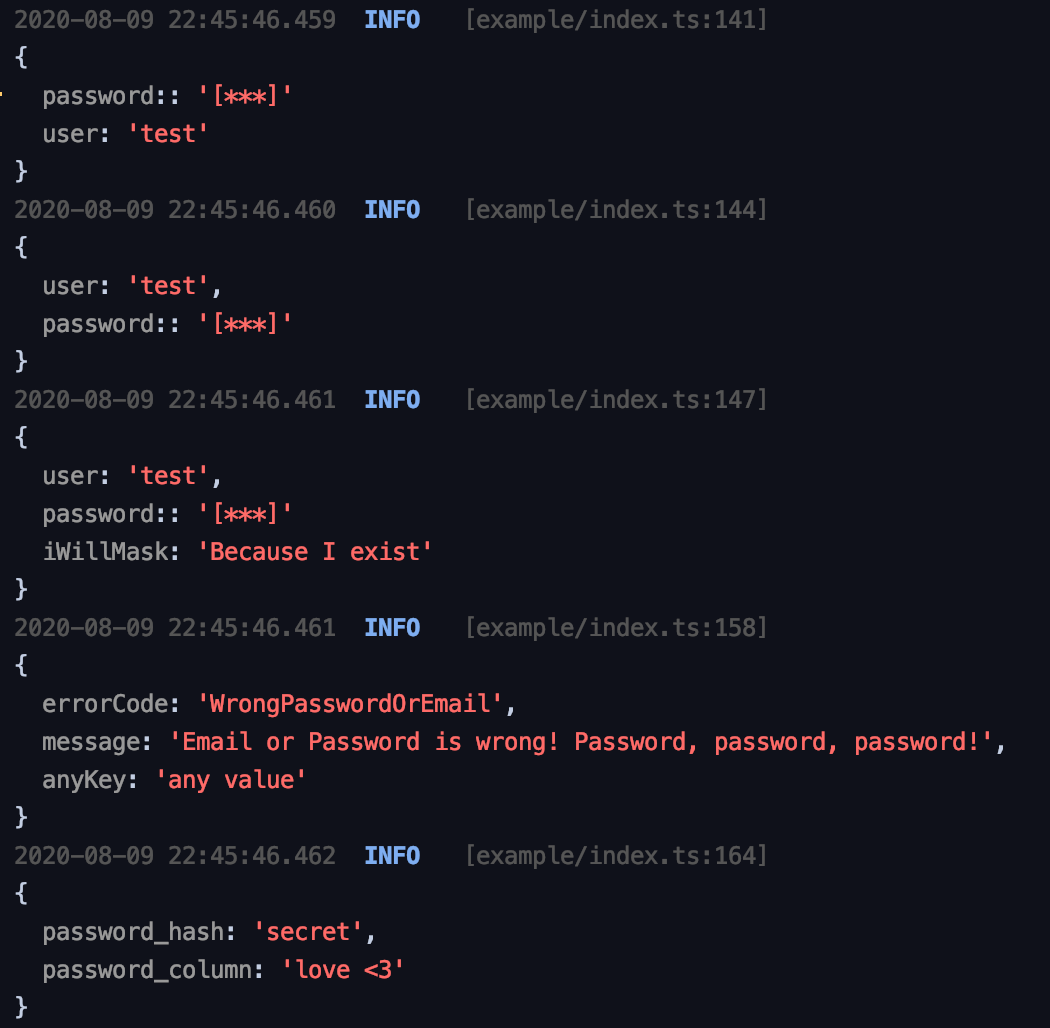
Btw. it’s not JSON anyways. JSON is a very limited representation of JS and many types are missing (e.g. BigInt). From the documentation:
util.inspect(object[, options])
I have released a new version
2.6.4that addresses this issue. Finally, there was only one question mark (?) missing in the RegEx. Thanks for pointing that out. Additionally, your screenshot indicated another problem with that RegEx that I also resolved. Your output should now look like this:I understand your point, however, masking happens for each and every log message and running a recursive search would lead to lower performance.
util.inspectis quite optimized when used once.