Order of Authenticator executions depends on credential order but not on order of Authentication Flow
See original GitHub issueDescribe the bug
We have a custom Authentication flow that follows the Identifier First pattern. In this flow we support passwordless authentication via WebAuthN as an alternative to plain passwords with 2FA. We want to use passwordless as primary authentication mechanism and allow users to choose password as another way to login.
For this we created the following authentication flow:
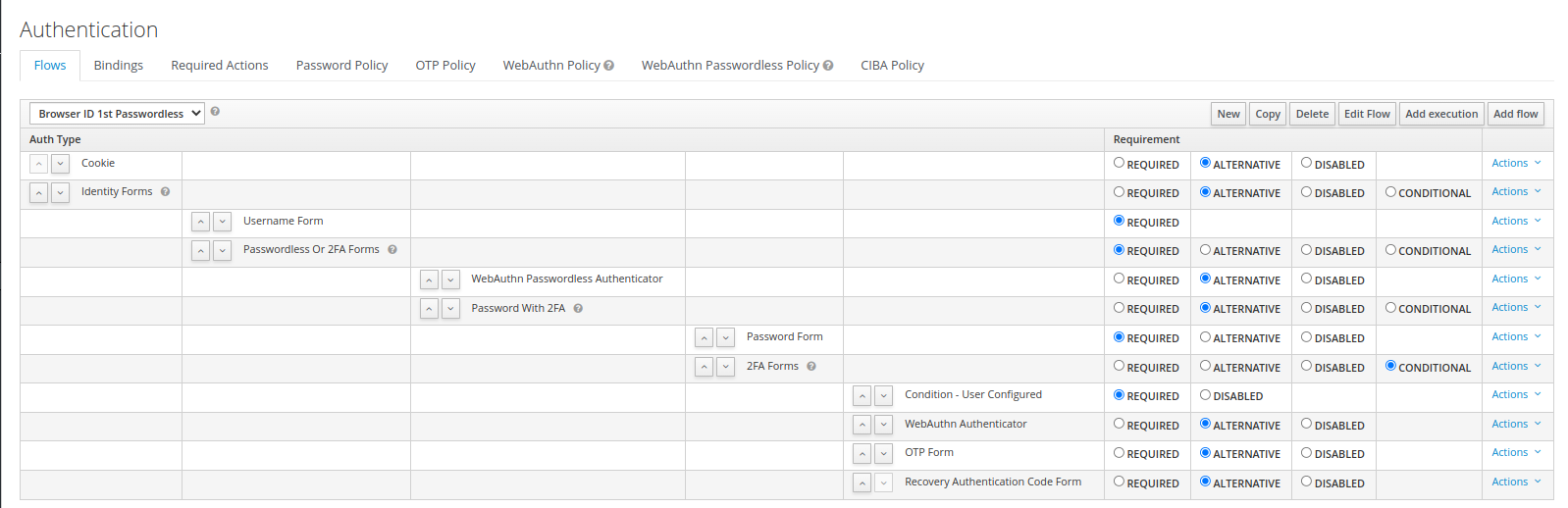
As shown in the flow - the passwordless authenticator is configured in a subflow before the password authenticator.
However the password authenticator is always executed first, as can be seen in the demo:

Version
18.0.0
Expected behavior
Passwordless authenticator should follow the username form authenticator.
Actual behavior
The Password form authenticator is shown after the username form authenticator. The user has to select “try another way” and select “Security Key” to execute the passwordless authenticator.
How to Reproduce?
See instructions in reproducer: https://github.com/thomasdarimont/keycloak-bugs/tree/main/keycloak-18-authflow-passwordless-orderbug
Anything else?
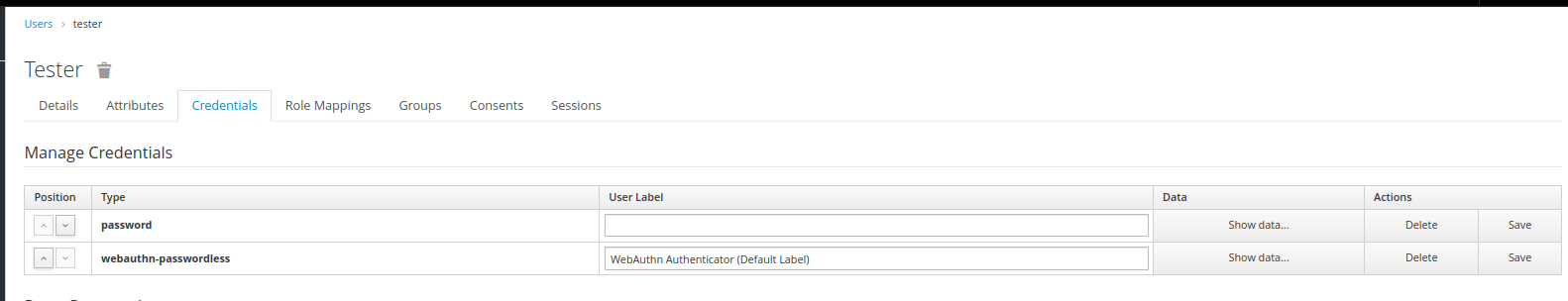
It seems that the order of the authenticator executions presented to the user is partially based on the order of the corresponding credentials. A credentials configuration with password first then followed by “passwordless” will yield the authenticator execution order shown above:
If I change the order of the credentials in the user configuration (passwordless before password)
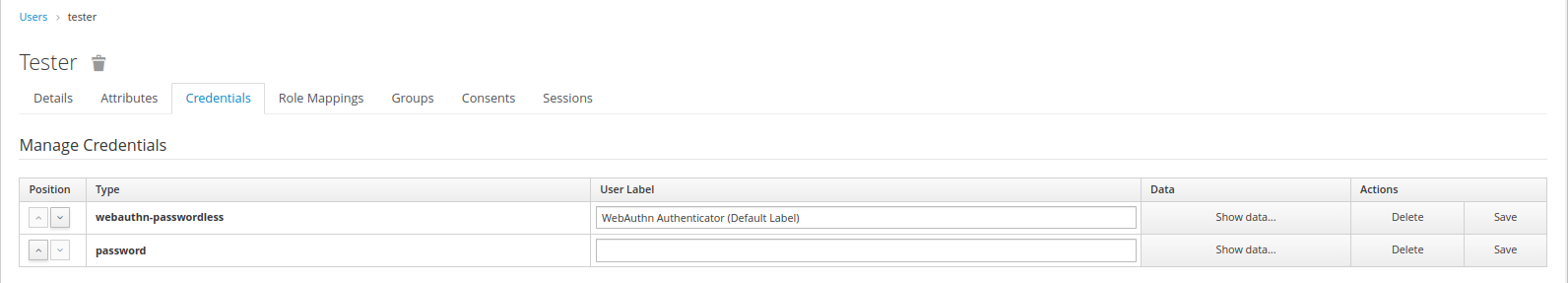
Then the authentication order is the one we expect:
I think this behaviour is quite confusing to a lot of users. IMHO the order of authenticator executions should primarily be determined by the ordering in the Authentication flow and not by the order of stored credential information.
I think the problem is caused by this code in the AuthenticationSelectionResolver#createAuthenticationSelectionList method.
FYI @mposolda
No response
Issue Analytics
- State:
- Created a year ago
- Reactions:4
- Comments:9 (8 by maintainers)

 Top Related StackOverflow Question
Top Related StackOverflow Question
@thomasdarimont WDYT about what Marek suggested? Do you have time to work on it?
@thomasdarimont @mabartos Thanks for bringing this issue. The original idea is, that the preferred order will be based on the “preferred credential” of the user. This is also described in the original design, which was created by the contributors of the authentication flow refactoring. See https://github.com/keycloak/keycloak-community/blob/main/design/multi-factor-admin-and-step-up.md#authentication-screens-for-the-user-in-a-browser-flow .
Right now, the ability to set the order of the credentials is supported only in the admin console, admin REST API and in the model. It was not yet done in the account console, so users themselves cannot change order of the credentials, however there is a plan to do this. See the discussion in the PR https://github.com/keycloak/keycloak/pull/8397 .
I afraid changing the order just based on the order in the authentication flow can work for you, but it may not be ideal for the others (EG. contributors of this original proposal).
How about changing like this: The order will be still based on the user preferred credential like it is now. But in case that there is same “priority” of the credential, it would be based on the order in the flow. In other words, credentials will be created with the same priority and hence the default order will be based on the order of the authentication flow. Just in case that user explicitly set his default credential in account console and/or admin changed the order in the admin console, then the order shown during authentication will be based on the priority set on the credential. Will this behaviour work for you?
I see that currently credentials are not created with the same priority - at least in the old model. See
JpaUserCredentialStore.createCredentialEntity. I recall that this was possibly done, so clicking the arrow in the admin console would always move the credential just one level up (or one level down). I propose we change this behaviour to create credentials with same priority (so it will possible that clicking arrow up/down will move credential up or down more than one level, but I think this is not big issue as admin console credentials tab may also change in the future and be aligned with the “default credential” approach rather than “arrows up/down” approach. WDYT?