Azure Key Vault task converts %3B in secrets to ;
See original GitHub issueRequired Information
Entering this information will route you directly to the right team and expedite traction.
Question, Bug, or Feature?
Type: Bug
Enter Task Name: AzureKeyVault@1 (https://github.com/microsoft/azure-pipelines-tasks/tree/master/Tasks/AzureKeyVaultV1)
Environment
- Server - Azure Pipelines
- Agent - Hosted,
windows-2019
Issue Description
The Azure Key Vault task is converting all instances of %3B in a secret to ;.
To reproduce, create a secret in a key vault with %3B in the value somewhere. Use the Azure Key Vault task to download the secret and observe that all instances of %3B in the value are converted to ;.
For the screenshots below I created a secret with the value a%3B:
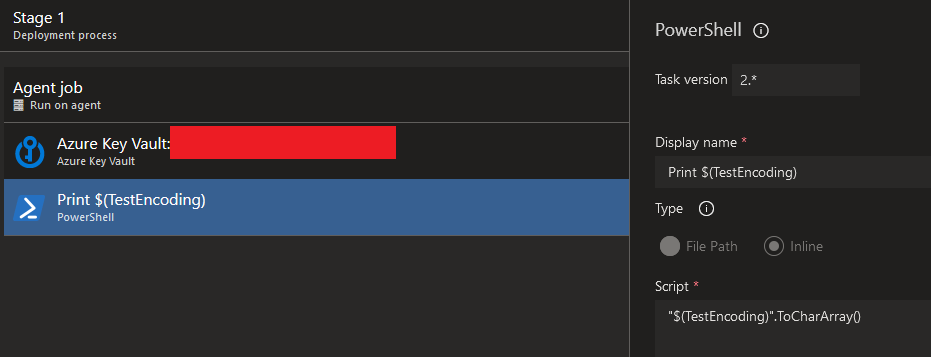
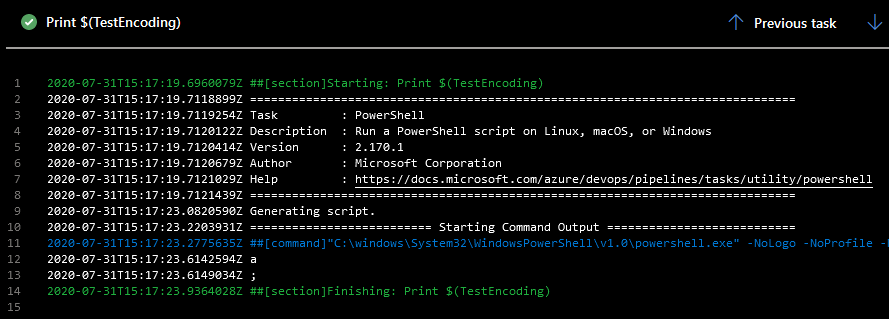
This issue seems to be isolated to the task because neither the Azure CLI nor the Azure PowerShell commandlets are affected:

Task logs
Pre-job: Azure Key Vault
2020-07-31T15:31:03.1714670Z SubscriptionId: lkjfdsalkjfdsa.
2020-07-31T15:31:03.1716309Z Key vault name: asdfjklasdfjkl.
2020-07-31T15:31:03.1717118Z ##[debug]set SYSTEM_UNSAFEALLOWMULTILINESECRET=true
2020-07-31T15:31:03.1731143Z ##[debug]Processed: ##vso[task.setvariable variable=SYSTEM_UNSAFEALLOWMULTILINESECRET;issecret=false;]true
2020-07-31T15:31:03.1732048Z ##[debug]Downloading selected secrets from subscriptionId: lkjfdsalkjfdsa, vault: asdfjklasdfjkl
2020-07-31T15:31:03.1734255Z ##[debug]Promise for downloading secret value for: TestEncoding
2020-07-31T15:31:03.1743918Z Downloading secret value for: TestEncoding.
2020-07-31T15:31:03.1776021Z ##[debug][POST]https://login.windows.net/***/oauth2/token/
2020-07-31T15:31:03.7384649Z ##[debug][GET]https://asdfjklasdfjkl.vault.azure.net/secrets/TestEncoding?api-version=2016-10-01
2020-07-31T15:31:03.9161950Z ##[debug]SYSTEM_DONOTMASKMULTILINESECRETS=undefined
2020-07-31T15:31:03.9164575Z ##[debug]set TestEncoding=********
2020-07-31T15:31:03.9186635Z ##[debug]Processed: ##vso[task.setvariable variable=TestEncoding;issecret=true;]***
2020-07-31T15:31:03.9191134Z ##[debug]set TestEncoding=********
2020-07-31T15:31:03.9199821Z ##[debug]Processed: ##vso[task.setvariable variable=TestEncoding;issecret=true;]***
2020-07-31T15:31:03.9202240Z ##[debug]task result: Succeeded
2020-07-31T15:31:03.9217134Z ##[debug]Processed: ##vso[task.complete result=Succeeded;]
2020-07-31T15:31:03.9493121Z ##[section]Finishing: Azure Key Vault: asdfjklasdfjkl
Error logs
The task does not produce any errors.
Issue Analytics
- State:
- Created 3 years ago
- Reactions:2
- Comments:7 (1 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
AzureKeyVault@2 - Azure Key Vault v2 task - Microsoft Learn
Use this task to download secrets, such as authentication keys, storage account keys, data encryption keys, .PFX files, and passwords from an ...
Read more >How to pass secrets downloaded from Azure KeyVault as ...
I've created a release pipeline in Azure that contains 3 tasks; the first two are run on an agent: 1. Deploy an Azure...
Read more >Inject Azure Key vault secrets into Azure DevOps Pipeline.
There are two way to retrieve secrets from Azure Key Vault into Pipelines. Pipeline Task – Secrets are available with in the pipeline...
Read more >Using Managed (System) Identities to access Azure Key Vault
Click on Azure role assignments to continue. 1-Identity. Click on Add role assignment followed by selecting the appropriate Subscription. From ...
Read more >Store the app secrets in Azure Key Vault and use during Azure ...
After all, the best way to keep a secret is not to tell anyone about it. This is where the Azure Key Vault...
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

It looks like the backtick symbol ( ` ) is also affected by this bug. If there is at least one backtick contained by the secret, we can meet these situations:
We are having the same issue. When retrieving Key Vault secrets that contain $ the incorrect value is returned to the pipeline causing login failures. We created two work arounds for this issue but would like to see the task code updated to correct the underlying problem.
What is the estimated time to get this issue fixed? Our team supports hundreds of pipelines across 100+ azure subscriptions and Key Vault is our primary secrets management service.