PowerShell will not allow me to enable unencrypted connections, due to missing Network Connection Profiles
See original GitHub issueSteps to reproduce
- Enable Hyper-V
- Install Cisco VPN client
- Install Proton VPN client
- Enable Windows Subsystem for Linux (WSL)
- Install Wireshark with NPCAP virtual adapter
C:\Users\TrevorSullivan> Set-Item -Path WSMan:\localhost\Service\AllowUnencrypted -Value true
Set-Item: WinRM firewall exception will not work since one of the network connection types on this machine is set to Public. Change the network connection type to either Domain or Private and try again.
C:\Users\TrevorSullivan> Get-NetConnectionProfile
Name : Andromeda
InterfaceAlias : Wi-Fi
InterfaceIndex : 3
NetworkCategory : Private
IPv4Connectivity : Internet
IPv6Connectivity : NoTraffic
C:\Users\TrevorSullivan> Enter-PSSession -ComputerName localhost
Enter-PSSession: Connecting to remote server localhost failed with the following error message : Access is denied. For more information, see the about_Remote_Troubleshooting Help topic.
Obviously, the Enter-PSSession command fails with Access is denied. I traced this back to the AllowUnencrypted setting on the WinRM service.

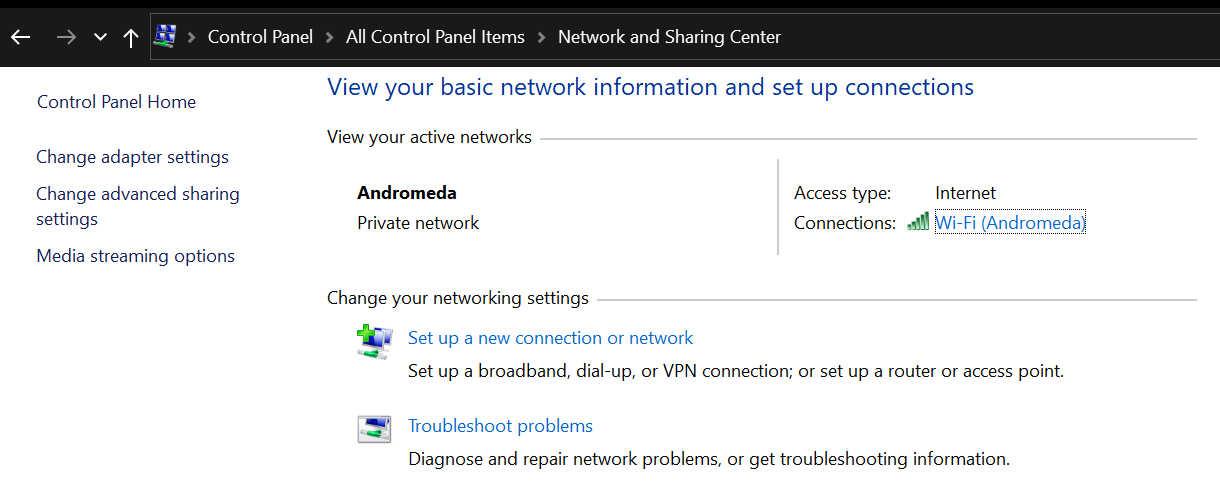
As you can see from the screenshots, the “Network Category” field is straight up missing for all but one of my network connections. Also, there’s only one connection profile returned by Get-NetConnectionProfile, and it’s already set to Private.
How am I supposed to discover which of my network connections is being detected as public?
Expected behavior
- Network Category is set for all network connections
Get-NetConnectionProfileshows me which of my networks ispublic- PowerShell sets WinRM configuration to allow unencrypted, without throwing any error messages
Actual behavior
PowerShell indicates that one of my network connections is public, although as best I can tell, none of them are set that way. There’s a conflict between what’s being reported by PowerShell and what’s being reported by Windows 10.
Environment data
Name Value
---- -----
PSVersion 7.0.3
PSEdition Core
GitCommitId 7.0.3
OS Microsoft Windows 10.0.19041
Platform Win32NT
PSCompatibleVersions {1.0, 2.0, 3.0, 4.0…}
PSRemotingProtocolVersion 2.3
SerializationVersion 1.1.0.1
WSManStackVersion 3.0
Issue Analytics
- State:
- Created 3 years ago
- Comments:5
 Top Results From Across the Web
Top Results From Across the Web
Security considerations for PowerShell Remoting using ...
This document covers security concerns, recommendations, and best practices when using PowerShell Remoting.
Read more >PowerShell remoting not working consistently
Enter-PSSession : Connecting to remote server PCName failed with the following error message : WinRM cannot complete the operation. Verify that ...
Read more >Enable PowerShell Remoting on a standalone (workgroup) ...
Enable PowerShell Remoting on a standalone (workgroup) computer.
Read more >Configuring PowerShell Remoting (WinRM) over HTTPS
The steps below describe how to configure a remote device running Windows you want to connect to using PowerShell Remoting over HTTPS. Make...
Read more >Configuring Devices for Monitoring via PowerShell
To enable SL1 to monitor Windows servers, you must first configure a user account on a Windows Server that SL1 can use to...
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

I was able to work around this problem by creating a self-signed certificate, and setting up an HTTPS listener for WinRM. That way, I don’t need to worry about enabling
AllowUnencrypted.Still, this should be considered a bug.
@SeeminglyScience good idea. I tried that code, and it seems to have set the category to private. However, PowerShell is still complaining. See below.
@SteveL-MSFT this might need to be passed along to the windows team responsible for this module; if their module is reporting incorrect information, it’ll make life difficult for folks trying to handle this kind of thing in any automated fashion.