pip 19.3 doesn't send client certificate
See original GitHub issueUbuntu 18.04 virtual environment
- pip version: 19.3
- Python version: 3.6.8
- OS: Ubuntu 18.04.3 LTS
We have a private Pypi server hosted with pypicloud. We use client certificates to authenticate users for downloading/uploading packages.
Description pip 19.3 doesn’t seem to send our client certificates so authentication fails and packages cannot be installed:
WARNING: Retrying (Retry(total=4, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLError(1, '[SSL: SSLV3_ALERT_HANDSHAKE_FAILURE] sslv3 alert handshake failure (_ssl.c:852)'),)': /simple/<our package name>/
I captured some of the SSL traffic from pip install in Wireshark and the client certificate option is there in the SSL handshake, but the certificates length is 0 with pip 19.3:
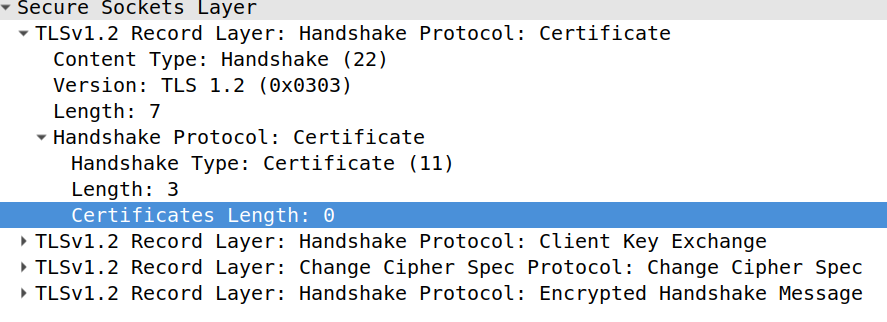
In 19.2.1, the length is non-zero and Wireshark shows the client certificate I expect.
Expected behavior We should not get an SSL error if our client certificates and CA certificates are not expired. I have checked our server logs there don’t appear to be any errors there with our certificates. If I downgrade to pip 19.2.1 or 19.2.3 in my virtual environment, then the SSL error goes away.
I also checked with the openssl s_client that a handshake succeeded with the same client certificate:
openssl s_client -connect <my server> -cert <cert> -key <key> -state
CONNECTED(00000005)
SSL_connect:before SSL initialization
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS write client hello
SSL_connect:SSLv3/TLS read server hello
depth=2 O = Digital Signature Trust Co., CN = DST Root CA X3
verify return:1
depth=1 C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3
verify return:1
depth=0 CN = <my server>
verify return:1
SSL_connect:SSLv3/TLS read server certificate
SSL_connect:SSLv3/TLS read server key exchange
SSL_connect:SSLv3/TLS read server certificate request
SSL_connect:SSLv3/TLS read server done
SSL_connect:SSLv3/TLS write client certificate
...
SSL handshake has read 4268 bytes and written 1546 bytes
Verification: OK
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID:
How to Reproduce
- Setup pip.conf or command-line arguments to use client certificate
- pip install <package>
- sslv3 alert handshake failure occurs
Output
pip install <my package>
Looking in indexes: https://pypi.org/simple/, https://<my server>/simple/
WARNING: Retrying (Retry(total=4, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLError(1, '[SSL: SSLV3_ALERT_HANDSHAKE_FAILURE] sslv3 alert handshake failure (_ssl.c:852)'),)': /simple/<my package>/
WARNING: Retrying (Retry(total=3, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLError(1, '[SSL: SSLV3_ALERT_HANDSHAKE_FAILURE] sslv3 alert handshake failure (_ssl.c:852)'),)': /simple/<my package>/
Issue Analytics
- State:
- Created 4 years ago
- Reactions:1
- Comments:7 (4 by maintainers)

 Top Related StackOverflow Question
Top Related StackOverflow Question
Ok, I think I have a container + script that reproduces the issue. It sets up its own CA and server/client certificates so it should be self-contained. I ran tshark in the Docker container and verified that when pip 19.3 talks to a dummy openssl server acting as pypi.org on the loopback interface, it doesn’t send the client cert.
It has something to do with the
trusted-hostparameter in /root/.pip/pip.conf. With that commented out, there’s no error. In the output below, some of the output from the openssl s_server process is mixed in with the script output (showing no client certificate sent).Dockerfile
pip.conf
repro.sh
Usage
Output
We’re using ~/.pip/pip.conf to specify the client certificates. I modified your
repo.shand was not able to reproduce the problem using our client + server certificates and a fake SSL server (instead of the python one, I wanted to disable TLS 1.3 so I could see the certificates being sent in Wireshark):openssl s_server -accept 8999 -www -cert server.pem -key server.key -CAfile ca-cert.pem -no_tls1_3 -Verify 1It’s a bit hard to produce something self-contained since we’ve got a Letsencrypt certificate tied to our own domain and a private PKI infrastructure for the client certificates.
It’s looking like it might be an issue when the client certificate bundle is specified in pip.conf, specifying on the command-line seemed to work fine in 19.3. I’ll try and come up with a new repro script that simulates this.