processSLO error. logout_not_success : AuthnFailure
See original GitHub issueHey Folks, I tried out the demo application , that was provided along with (using okta as Idp). SSO works perfectly, but SLO Fails with an error error. logout_not_success . When I tried debugging, It was found that the status returned was AuthnFailure .
-
The
onelogin.saml.propertiesfile is attached. onelogin.saml.properties.txt -
okta saml setttings :
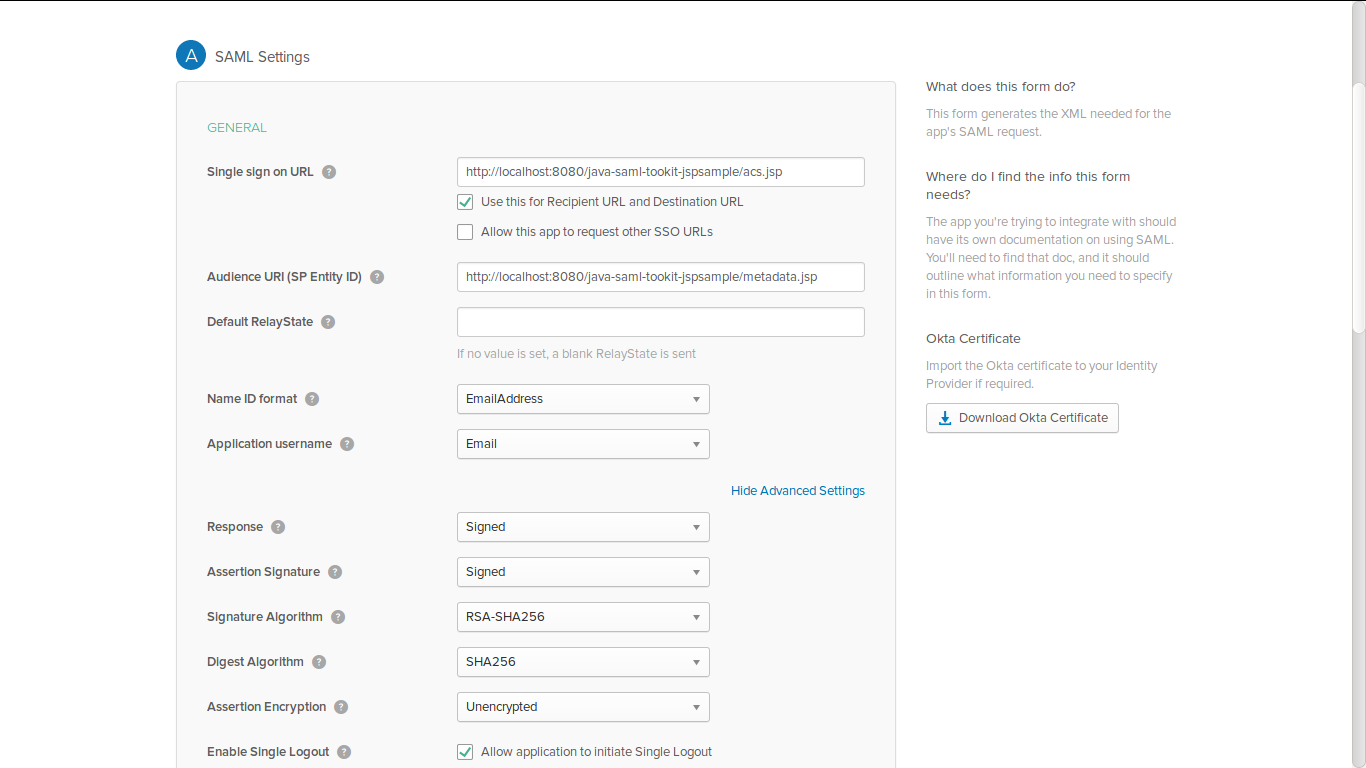
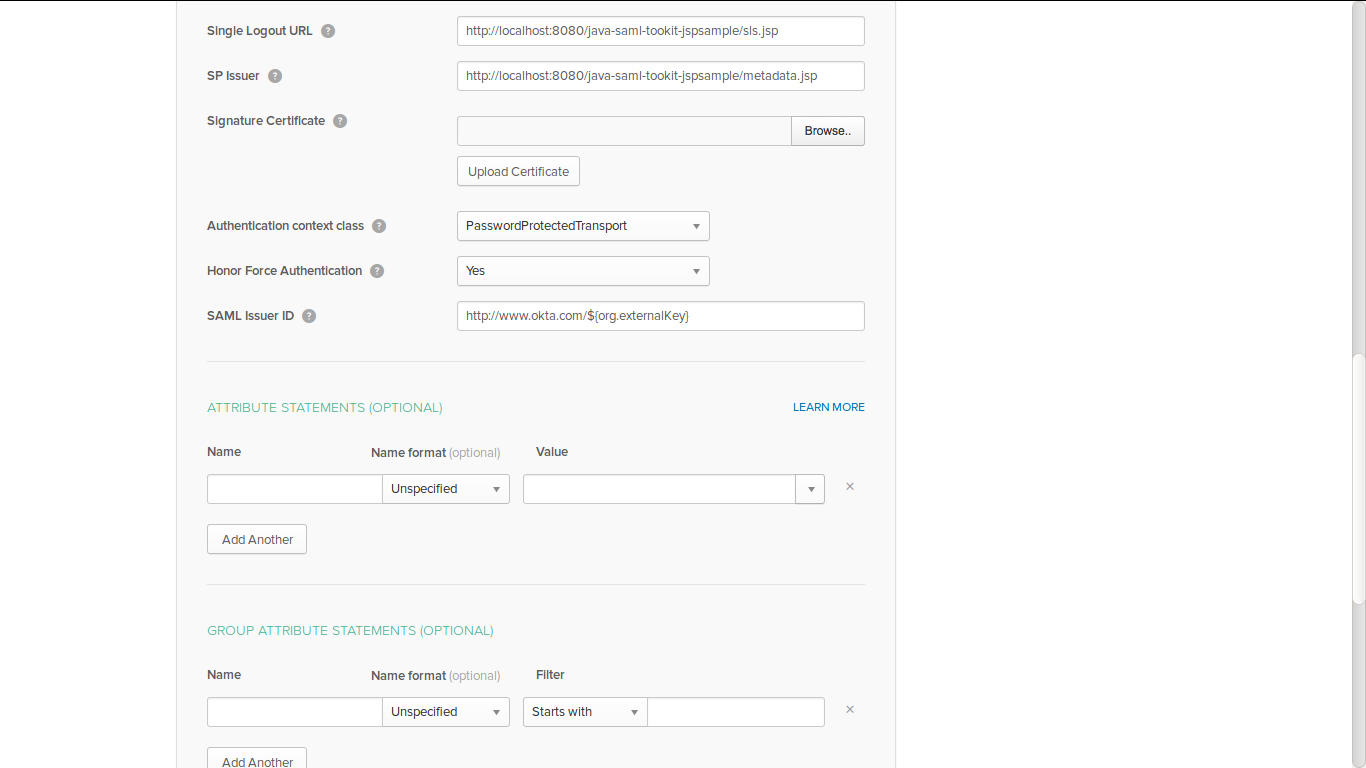
-
All keys (private & public) : OneLoginSpAllKeys.txt
PS: SP private key added in onelogin.saml.properties and certificate uploaded in okta (for SLO)
What could have went wrong ?
Issue Analytics
- State:
- Created 6 years ago
- Comments:6 (2 by maintainers)
 Top Results From Across the Web
Top Results From Across the Web
processSLO error. logout_not_success : AuthnFailure #127
When I tried debugging, It was found that the status returned was AuthnFailure . The onelogin.saml.properties file is attached. onelogin.saml.
Read more > Top Related Medium Post
Top Related Medium Post
No results found
 Top Related StackOverflow Question
Top Related StackOverflow Question
No results found
 Troubleshoot Live Code
Troubleshoot Live Code
Lightrun enables developers to add logs, metrics and snapshots to live code - no restarts or redeploys required.
Start Free Top Related Reddit Thread
Top Related Reddit Thread
No results found
 Top Related Hackernoon Post
Top Related Hackernoon Post
No results found
 Top Related Tweet
Top Related Tweet
No results found
 Top Related Dev.to Post
Top Related Dev.to Post
No results found
 Top Related Hashnode Post
Top Related Hashnode Post
No results found

The Logout Request seems to be unsigned. I mean , there is no signature information in the SAML Request :
If so, What might be the reason , I generated the keys using OneLogin Certificate Generator
Hi Pitbull and sreeharibs ,
I am facing same AuthnFailure issue. simpleSAMLPHP is SP and okta is IDP,
Even I am not gettting which Signature Certificate I suppos to upload when I enable singlesignout url.
I newbie in SAML. Please help.
Here is Logout Request
<samlp:AuthnRequest xmlns:samlp=“urn:oasis:names:tc:SAML:2.0:protocol” xmlns:saml=“urn:oasis:names:tc:SAML:2.0:assertion” ID=“_80a5b27cf6125709cf03471025c7f3e54c300ffeed” Version=“2.0” IssueInstant=“2018-09-05T11:57:34Z” Destination=“https://harbingergroup-2018.okta.com/app/harbingergrouporg336712_checksterportalsamlexample_1/exk1dy6fwqo8pKSsT356/sso/saml” AssertionConsumerServiceURL=“http://localhost/simplesaml/module.php/saml/sp/saml2-acs.php/portal-okta-com” ProtocolBinding=“urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST” > saml:Issuerhttp://localhost/simplesaml/module.php/saml/sp/metadata.php/portal-okta-com</saml:Issuer> <samlp:NameIDPolicy Format=“urn:oasis:names:tc:SAML:2.0:nameid-format:transient” AllowCreate=“true” /> </samlp:AuthnRequest>
Logout response <saml2p:Response xmlns:saml2p=“urn:oasis:names:tc:SAML:2.0:protocol” Destination=“http://localhost/simplesaml/module.php/saml/sp/saml2-acs.php/portal-okta-com” ID=“id113224923057177621748603245” InResponseTo=“_80a5b27cf6125709cf03471025c7f3e54c300ffeed” IssueInstant=“2018-09-05T11:58:38.760Z” Version=“2.0” xmlns:xs=“http://www.w3.org/2001/XMLSchema” > <saml2:Issuer xmlns:saml2=“urn:oasis:names:tc:SAML:2.0:assertion” Format=“urn:oasis:names:tc:SAML:2.0:nameid-format:entity” >http://www.okta.com/exk1dy6fwqo8pKSsT356</saml2:Issuer> <ds:Signature xmlns:ds=“http://www.w3.org/2000/09/xmldsig#”> ds:SignedInfo <ds:CanonicalizationMethod Algorithm=“http://www.w3.org/2001/10/xml-exc-c14n#” /> <ds:SignatureMethod Algorithm=“http://www.w3.org/2001/04/xmldsig-more#rsa-sha256” /> <ds:Reference URI=“#id113224923057177621748603245”> ds:Transforms <ds:Transform Algorithm=“http://www.w3.org/2000/09/xmldsig#enveloped-signature” /> <ds:Transform Algorithm=“http://www.w3.org/2001/10/xml-exc-c14n#”> <ec:InclusiveNamespaces xmlns:ec=“http://www.w3.org/2001/10/xml-exc-c14n#” PrefixList=“xs” /> </ds:Transform> </ds:Transforms> <ds:DigestMethod Algorithm=“http://www.w3.org/2001/04/xmlenc#sha256” /> ds:DigestValueRonGvjr/rJN879X9cfHDCAm9Myw2/srlKgD66DiMUZg=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> ds:SignatureValueabMC6TzURXmOk4WOQLGLEBfFlEKwepHDe3EhNbDvdFB2pkzH3Y01Y5l95nl+5YaQLxX5CNQnJLnI2I8Gdq3h/BoYjtz3GutbF5LnyW/GvYfgoJpAn5JncUZE6HiHX3/mjA42vtmjuHspQvAc4T2wHTZbp4PgrhVh+oDcffUqA50Ya2LLUjtO3KuOKFzosmMvXc9oieW9XpkSJoucfL8yUEB4bD9Ii29tr93ml0Dcn0hH/RBsu2f0Dm9WN0vZicMiZEf4susFWfUbffzZCIqIPQwqYtL9Gxs4e0XZ1r7mc+CwwPt71PT72z0HXS2Jz/hyqE4Vw8fuQA7ztZxOObotyg==</ds:SignatureValue> ds:KeyInfo ds:X509Data ds:X509CertificateMIIDtjCCAp6gAwIBAgIGAWU32Q8wMA0GCSqGSIb3DQEBCwUAMIGbMQswCQYDVQQGEwJVUzETMBEG A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU MBIGA1UECwwLU1NPUHJvdmlkZXIxHDAaBgNVBAMME2hhcmJpbmdlcmdyb3VwLTIwMTgxHDAaBgkq hkiG9w0BCQEWDWluZm9Ab2t0YS5jb20wHhcNMTgwODE0MDk1MDM2WhcNMjgwODE0MDk1MTM2WjCB mzELMAkGA1UEBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lz Y28xDTALBgNVBAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRwwGgYDVQQDDBNoYXJiaW5n ZXJncm91cC0yMDE4MRwwGgYJKoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0B AQEFAAOCAQ8AMIIBCgKCAQEArGs+8/4nBiE+ThGlNt3wQ3Ps0WrPOtLwBQsxyC4WvXUt+/kQE7Lg 5kbQY0f+PGFstycH0jE2y0wy3nlUO6oRVXbqoLpgG1s8mXvaJApA4zPcY7WOcWN8Q4nkgy9hoGnk FkKI0aiDZ6y1qnHW1pHGQQWmVFY+GIfRktN7CBltlvbTHnUi4fykokX5Lu0flBBkzJOtqQVbSYUa 3t7PY2XwK6bOBkEyHvo6+B5cOJUEZRHD212TTQXL5znsA9haHt7ySdJkzVDJqw24yLR3ESAgPqPY bgkl1J536xPQler3EIRqPzPqYZv6sG2mNiJB4FIAYeiHFEKdNEo03CXEnn/iBQIDAQABMA0GCSqG SIb3DQEBCwUAA4IBAQB1tpPt9mMMreE7wXoMQ8VTXZStKex0StdMu83I3uROXzMkqdGPrfEgNXXu WzDwkknhDrbRi3pQeruNgFNbrHB0aQV+wizle30YRo/HDtxvwIP/wHwAzEI36P8HNEdJzUcZLebZ d8kXl2ly4eHSmE0FtG8qcneVyPg0+YddUA+4O845+Zb8cgaFmcl2KRXFNMI7tTAV4ah28gHsUXRL 0+B8S6Br0jrmfGAY28lODiFgXZEy8vAortbsJkJZuUaaqgQj3BckWyImnCgaLu6A1lmNCBwAih+d RFAkYVpa0PRhm68DYlmGbRfjmvGlYIAWwYBXzywqhPhkDDtN2No1LkBl</ds:X509Certificate> </ds:X509Data> </ds:KeyInfo> </ds:Signature> <saml2p:Status xmlns:saml2p=“urn:oasis:names:tc:SAML:2.0:protocol”> <saml2p:StatusCode Value=“urn:oasis:names:tc:SAML:2.0:status:Success” /> </saml2p:Status> <saml2:Assertion xmlns:saml2=“urn:oasis:names:tc:SAML:2.0:assertion” ID=“id11322492305794143304208408” IssueInstant=“2018-09-05T11:58:38.760Z” Version=“2.0” xmlns:xs=“http://www.w3.org/2001/XMLSchema” > <saml2:Issuer Format=“urn:oasis:names:tc:SAML:2.0:nameid-format:entity” xmlns:saml2=“urn:oasis:names:tc:SAML:2.0:assertion” >http://www.okta.com/exk1dy6fwqo8pKSsT356</saml2:Issuer> <ds:Signature xmlns:ds=“http://www.w3.org/2000/09/xmldsig#”> ds:SignedInfo <ds:CanonicalizationMethod Algorithm=“http://www.w3.org/2001/10/xml-exc-c14n#” /> <ds:SignatureMethod Algorithm=“http://www.w3.org/2001/04/xmldsig-more#rsa-sha256” /> <ds:Reference URI=“#id11322492305794143304208408”> ds:Transforms <ds:Transform Algorithm=“http://www.w3.org/2000/09/xmldsig#enveloped-signature” /> <ds:Transform Algorithm=“http://www.w3.org/2001/10/xml-exc-c14n#”> <ec:InclusiveNamespaces xmlns:ec=“http://www.w3.org/2001/10/xml-exc-c14n#” PrefixList=“xs” /> </ds:Transform> </ds:Transforms> <ds:DigestMethod Algorithm=“http://www.w3.org/2001/04/xmlenc#sha256” /> ds:DigestValueqgq3vyLpvbB4qTmYY4SubDOujV3SoP6aYwB15cI05jE=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> ds:SignatureValuePtjAue49GCGMe1J5eKhAlCO0TOuSJiA21iPrTU1l3NIRxnT3Ot2vzQRvSRJp5+GR8B+SIoq12X5asw6VZ29W7oZgGHHKAAum3V4DUyUCmZsupA444LCw1Thv3QyMlT4+1ANDXKjrJgabeft3JNw3kdkAB5RXWV6ovooq3jar4cxbPlqEe2D+G627NeAh4OKIqnbsEOx+bX7faA4uzXFvkGTTPhA06Afj8NwvBQZtZF3HA70Mr6WQ2mx52Rkl/jwOsD3uJnSJvfe3bQ0YJ+9tltyKu+IraE6jRS0u5pZJy3iE4eaC81qMtJd3mt9fBazUAO/0V3g9Q4hfyuY7loCWvg==</ds:SignatureValue> ds:KeyInfo ds:X509Data ds:X509CertificateMIIDtjCCAp6gAwIBAgIGAWU32Q8wMA0GCSqGSIb3DQEBCwUAMIGbMQswCQYDVQQGEwJVUzETMBEG A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU MBIGA1UECwwLU1NPUHJvdmlkZXIxHDAaBgNVBAMME2hhcmJpbmdlcmdyb3VwLTIwMTgxHDAaBgkq hkiG9w0BCQEWDWluZm9Ab2t0YS5jb20wHhcNMTgwODE0MDk1MDM2WhcNMjgwODE0MDk1MTM2WjCB mzELMAkGA1UEBhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lz Y28xDTALBgNVBAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRwwGgYDVQQDDBNoYXJiaW5n ZXJncm91cC0yMDE4MRwwGgYJKoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0B AQEFAAOCAQ8AMIIBCgKCAQEArGs+8/4nBiE+ThGlNt3wQ3Ps0WrPOtLwBQsxyC4WvXUt+/kQE7Lg 5kbQY0f+PGFstycH0jE2y0wy3nlUO6oRVXbqoLpgG1s8mXvaJApA4zPcY7WOcWN8Q4nkgy9hoGnk FkKI0aiDZ6y1qnHW1pHGQQWmVFY+GIfRktN7CBltlvbTHnUi4fykokX5Lu0flBBkzJOtqQVbSYUa 3t7PY2XwK6bOBkEyHvo6+B5cOJUEZRHD212TTQXL5znsA9haHt7ySdJkzVDJqw24yLR3ESAgPqPY bgkl1J536xPQler3EIRqPzPqYZv6sG2mNiJB4FIAYeiHFEKdNEo03CXEnn/iBQIDAQABMA0GCSqG SIb3DQEBCwUAA4IBAQB1tpPt9mMMreE7wXoMQ8VTXZStKex0StdMu83I3uROXzMkqdGPrfEgNXXu WzDwkknhDrbRi3pQeruNgFNbrHB0aQV+wizle30YRo/HDtxvwIP/wHwAzEI36P8HNEdJzUcZLebZ d8kXl2ly4eHSmE0FtG8qcneVyPg0+YddUA+4O845+Zb8cgaFmcl2KRXFNMI7tTAV4ah28gHsUXRL 0+B8S6Br0jrmfGAY28lODiFgXZEy8vAortbsJkJZuUaaqgQj3BckWyImnCgaLu6A1lmNCBwAih+d RFAkYVpa0PRhm68DYlmGbRfjmvGlYIAWwYBXzywqhPhkDDtN2No1LkBl</ds:X509Certificate> </ds:X509Data> </ds:KeyInfo> </ds:Signature> <saml2:Subject xmlns:saml2=“urn:oasis:names:tc:SAML:2.0:assertion”> <saml2:NameID Format=“urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress”>sujay@harbingergroup.com</saml2:NameID> <saml2:SubjectConfirmation Method=“urn:oasis:names:tc:SAML:2.0:cm:bearer”> <saml2:SubjectConfirmationData InResponseTo=“_80a5b27cf6125709cf03471025c7f3e54c300ffeed” NotOnOrAfter=“2018-09-05T12:03:38.760Z” Recipient=“http://localhost/simplesaml/module.php/saml/sp/saml2-acs.php/portal-okta-com” /> </saml2:SubjectConfirmation> </saml2:Subject> <saml2:Conditions NotBefore=“2018-09-05T11:53:38.760Z” NotOnOrAfter=“2018-09-05T12:03:38.760Z” xmlns:saml2=“urn:oasis:names:tc:SAML:2.0:assertion” > saml2:AudienceRestriction saml2:Audiencehttp://localhost/simplesaml/module.php/saml/sp/metadata.php/portal-okta-com</saml2:Audience> </saml2:AudienceRestriction> </saml2:Conditions> <saml2:AuthnStatement AuthnInstant=“2018-09-05T11:58:37.765Z” SessionIndex=“_80a5b27cf6125709cf03471025c7f3e54c300ffeed” xmlns:saml2=“urn:oasis:names:tc:SAML:2.0:assertion” > saml2:AuthnContext saml2:AuthnContextClassRefurn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml2:AuthnContextClassRef> </saml2:AuthnContext> </saml2:AuthnStatement> <saml2:AttributeStatement xmlns:saml2=“urn:oasis:names:tc:SAML:2.0:assertion”> <saml2:Attribute Name=“FirstName” NameFormat=“urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified” > <saml2:AttributeValue xmlns:xs=“http://www.w3.org/2001/XMLSchema” xmlns:xsi=“http://www.w3.org/2001/XMLSchema-instance” xsi:type=“xs:string” >Sujay</saml2:AttributeValue> </saml2:Attribute> <saml2:Attribute Name=“LastName” NameFormat=“urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified” > <saml2:AttributeValue xmlns:xs=“http://www.w3.org/2001/XMLSchema” xmlns:xsi=“http://www.w3.org/2001/XMLSchema-instance” xsi:type=“xs:string” >K</saml2:AttributeValue> </saml2:Attribute> <saml2:Attribute Name=“Email” NameFormat=“urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified” > <saml2:AttributeValue xmlns:xs=“http://www.w3.org/2001/XMLSchema” xmlns:xsi=“http://www.w3.org/2001/XMLSchema-instance” xsi:type=“xs:string” >sujay@harbingergroup.com</saml2:AttributeValue> </saml2:Attribute> </saml2:AttributeStatement> </saml2:Assertion> </saml2p:Response>