Auth support for SameSite Changes coming to Browsers and Loading CCP widget on a 3rd Party Domain
See original GitHub issueAs of Chrome v80 – to be released Feb 4 - (and soon to be Firefox and the latest IE) the browsers will be enforcing SameSite cookies by default. Meaning that if SameSite policy is not set on cookies they will by default not be available across third party domains. This is problematic for any developers trying to embed AWS connect widget’s on one of their 3rd party domains.
Better explanation: https://web.dev/samesite-cookies-explained/#explicitly-state-cookie-usage-with-the-samesite-attribute
The SAML auth flow with AWS connect currently obtains the following auth cookies after SAML auth flow with a API call to
POST https://${ConnectInstance}.awsapps.com/connect/auth/sign-in
This API call set the 2 following cookies on Response used for authentication on subsequent AWS Connect Calls
lily-auth-prod-iad && lily-auth-refresh-prod-iad
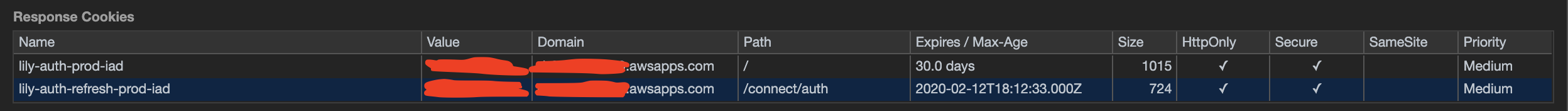
As you can see these cookies are being set with SameSite as empty. This causes Chrome in new version to default cookies SameSite policy to SameSite=Lax which then will cause these auth cookies to not be sent to the subsequent AWS call to authorize with how the CCP widget is loaded into an IFRAME on a 3rd party domain.
GET https://${ConnnectInstance}.awsapps.com/connect/auth/authorize
By downloading chrome canary version you can validate this breaks as well as get the following warning saying cookies are being filtered so they will not be sent along with the call to /connect/auth/authorize and thus we get a 401 consistently.
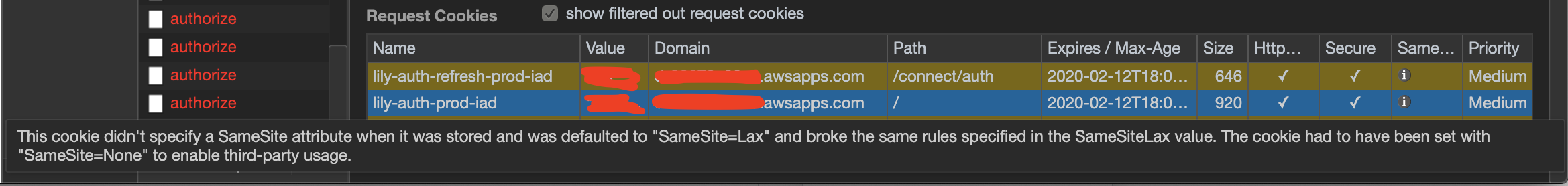
To Test:
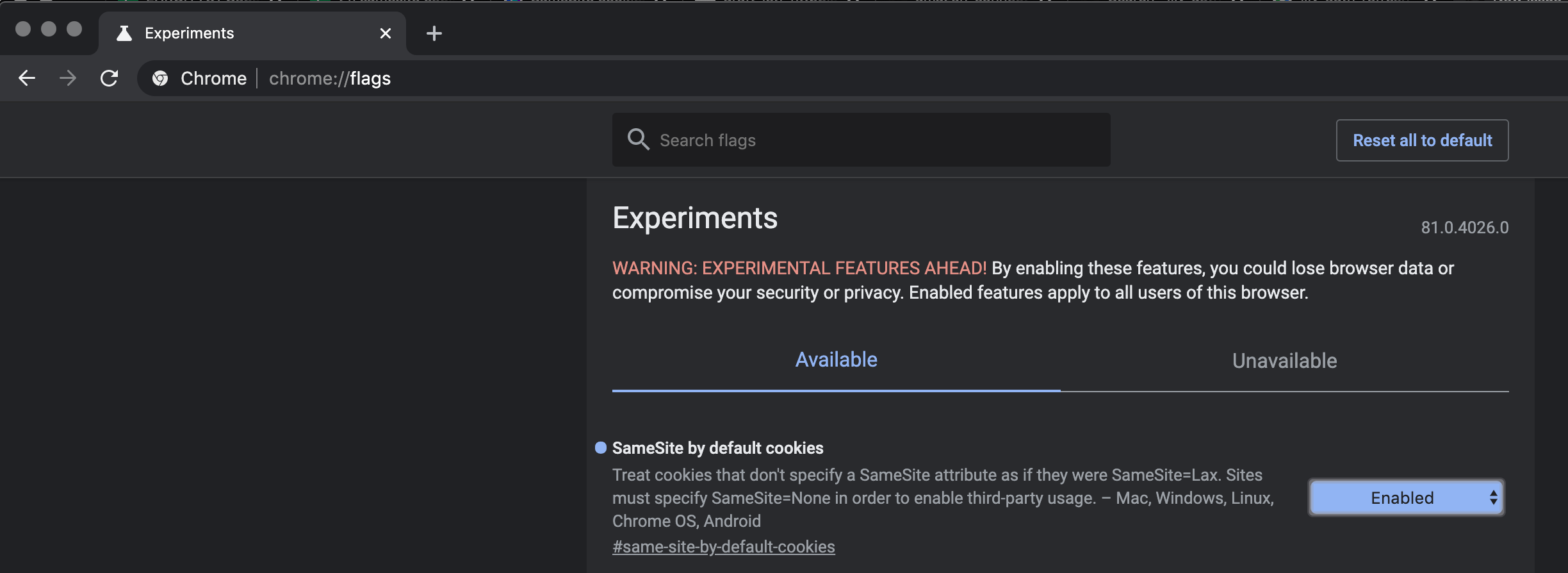
- Download Chrome Canary ( https://www.google.com/chrome/canary/ )
- In your current Chrome type in chrome://flags, and enable SameSite cookies
Is there any recommendation for developers to work around this or for how to proceed if they are embedding the CCP widget on a custom domain name. This would be a change Amazon would need to make with how they are defaulting cookies on the call to /connect/auth/sign-in and set connect auth cookies to SameSite=None if they intend to allow end users to embed the aws connect CCP widget on their domains.
Issue Analytics
- State:
- Created 4 years ago
- Reactions:12
- Comments:10 (5 by maintainers)

 Top Related StackOverflow Question
Top Related StackOverflow Question
Thanks for the detailed post!
We are aware of this issue and are working on a solution, stay tuned for an update.
@scoland Will this fix be compatible with “older” amazon-connect-streams versions and done in CCP code or do we need to upgrade our client installations?
Thanks for any information that helps us to prevent outages.