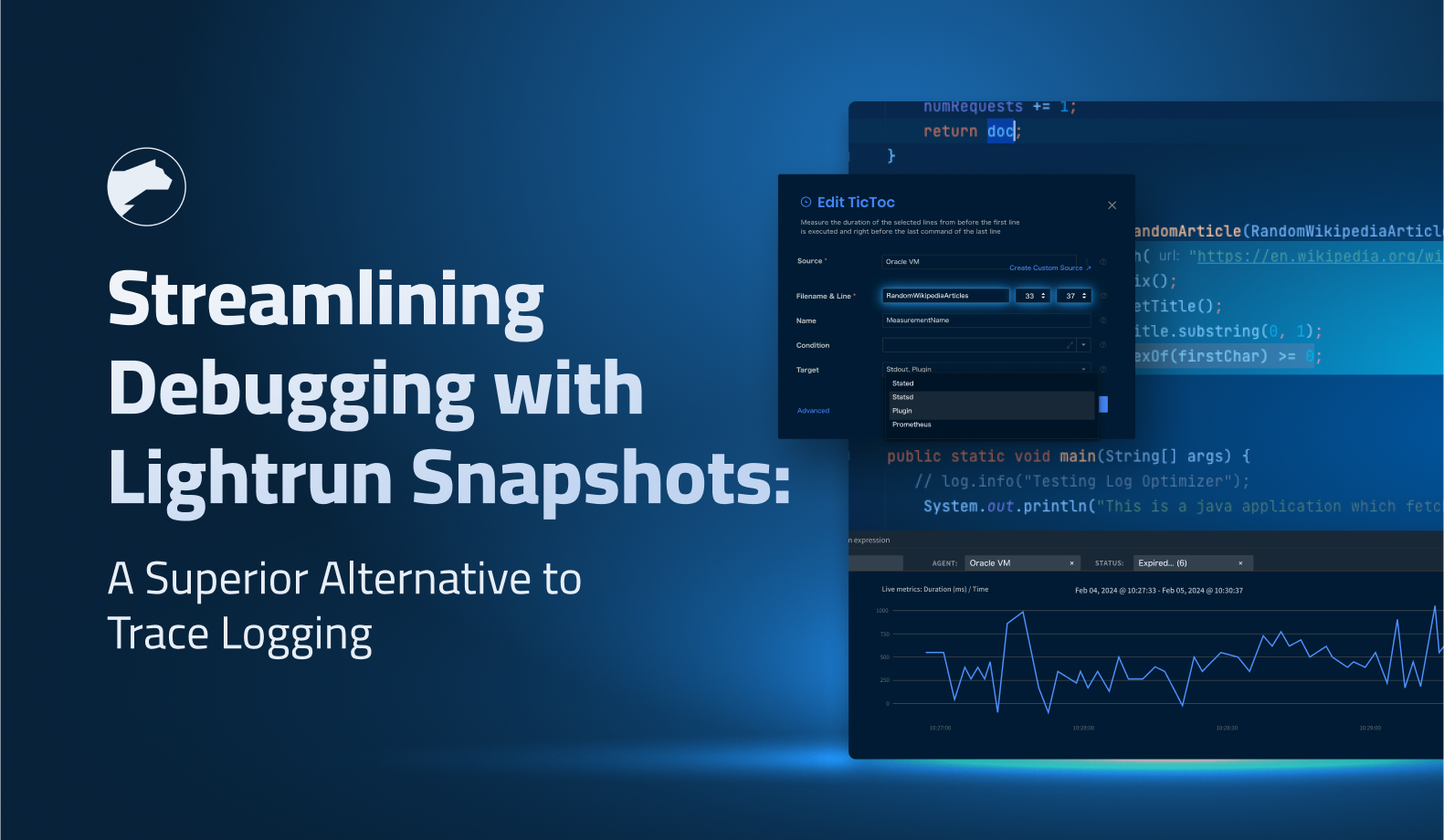
Best Practices for Using JIT Access as Part of Developer Observability
Introduction
JIT Access, sometimes referred to as just-in-time provisioning or just-in-time privileged access management (JIT PAM), is a security strategy that grants users access privileges for limited time periods. Access is granted on an “as-needed” basis. For example, if a developer requires access to a specific platform for a week or as part of an on-call access to production duty, a JIT Access system can provide that access and automatically revoke it after the time period ends. The primary aim of JIT Access is to reduce the risk associated with standing privileges, which are continuous access rights that can be exploited by malicious users. According to a research by Microsoft, less than 2% of permissions granted to super identities are actually used, hence, exposing the organizations to unnecessary risks.
Effective JIT Access must deliver precise, temporary access quickly and efficiently. This necessitates automation through some public API for managing users’ accessibility. In this blog, we will dive deep into the benefits of employing a JIT system and how it can effectively help organizations as part of their developer observability workflows.
Benefits of JIT Access for Developers
Organizations that adopt and use JIT as part of their software development lifecycle and within their observability and troubleshooting processes enjoy a myriad of benefits that includes:
- Minimize vulnerability to external security risks that can affect the business by granting unnecessary security permissions to sensitive environments
- Mitigating internal risk exposure by reducing the level of insider security threats to the business
- Enforcing the PoLP (principle of least privilege) which is an imperative in today’s complex software development environment.
- IT and developer productivity are properly balanced. By enforcing JIT organizations can significantly reduce the overhead and administrative burden on IT.
- Adherence to security policy and improving organizational auditability by being on top of internal developers’ access to highly sensitive environments (Production, pre-production, etc.)
Lightrun JIT Access Introduction
The Lightrun platform fully supports JIT (Just-In-Time) access in addition to its comprehensive suite of security features, including SCIM, RBAC, and Agent Pools. The JIT access feature is enabled through a public API, facilitating seamless automation and integration with internal systems. It is also accessible via the Lightrun management portal (as shown in the screenshot below). Within the management server UI, Lightrun distinguishes between 2 access types: Administrative permissions and Platform permissions. The administrative permissions refers to the login access to the Lightrun platform, user management, and service configuration. The platform permissions that allow developers to retrieve data including Logs, Snapshots, and Metrics from the customer applications, are managed via RBAC and are subject to the JIT access.
To get started with the Lightrun JIT please ensure that you have the RBAC security features enabled in your platform, and that you have created the right debugging agent-pools to be used within your different engineering groups.
Please note that Lightrun supports two use-cases:
- Temp Access – This use case is suitable when a developer requires access for a relatively short term, with the duration known in advance
- RBAC API – This use case manages “steady state” permissions by adding or removing users from groups, controlling their access to agent pools. It integrates Lightrun permissions with customer systems for long-term access management, not just for short-term grants.
Best Practices of Using Lightrun JIT
As mentioned above, Lightrun developer observability platform fully supports JIT as part of its enterprise grade security features. Customers that need to perform live debugging of their incidents across environments can enjoy both the API and the UI-Based JIT implementation to grant access to specific developers across different agent-pools across deployments for a given time period. Once the time elapses the developers are no longer eligible to access these environments, hence, organizations can safeguard their systems and protect them from any malicious attack.
A solid implementation and utilization of a JIT system should adhere to the following principles:
- Least Privilege Principle: Users should be granted the minimum level of access necessary to perform their tasks.
- Time-based Access: Access rights should be time-bound, ensuring they are automatically revoked once no longer needed.
- Audit and Compliance: All access requests and grants should be logged and monitored to maintain compliance and enable audits.
- User-friendly Automation: The system should be automated but also intuitive for users to request and receive access without extensive delays or complexities.
- Scalability: The solution should scale with the organization’s size and access needs, maintaining performance as demand grows.
With the above principles in mind, it is important to then follow a streamlined process of implementation and maintenance of the JIT within the organization.
The process should consist of 3 main pillars:
- Assessment phase → That is when administrators gain visibility into which users require which level of access and permissions to which environment, and for how long. This can be an organizational “template” or policy that is being created and triggered every time it is needed to make this an automated process.
- JIT Execution – This is a critical phase within the JIT implementation process. Simplifying the process of granting users access to environments should be done in an automated fashion making it simple and accessible to the developers to ask for specific permissions to specific environments. To properly utilize JIT, organizations should ensure it’s integrated with the incident response/management flow. As an example, when a developer is tasked to handle an incident, part of the flow can be granting temporary Lightrun privileges for the service/application which need to be debugged. Tools like servicenow and pagerduty can call REST APIs as part of the incident response flow.
- JIT Maintainability – This step is fundamental since it ensures a continuous and proper utilization of your JIT implementation. Consider regular audits and monitor system logs to ensure that the usage is as intended across all users and environments.
By following these principles, organizations can implement JIT Access effectively, balancing security with operational efficiency.
Bottom Line
In today’s complex software development processes, JIT and enterprise grade security policies are critical to protect the business while not interfering with the agility that developers need to access environments as part of solving critical issues or supporting a customer issue. With that in mind, it is also important to understand the challenges, benefits, and best practices of a JIT implementation.
Another critical pillar and benefit of using JIT as part of software debugging workflow is the ephemeral permission nature of it as well as the ability to integrate the process to internal engineering incident management systems (JIRA, Zephyr, etc.). Such integration can provide important audit trails and correlation between the incidents and the actions that were taken to resolve them.
To learn more about JIT and how Lightrun’s JIT solution can help with your live debugging capabilities while protecting your business, please visit the Lightrun documentation.
It’s Really not that Complicated.
You can actually understand what’s going on inside your live applications.