Securing Your Applications: A Guide to Log Injection Prevention
Introduction
Log injection is a well-known vulnerability that can pose serious threats to the security of your applications. In this blog post, we will explore what log injection is, why it’s a concern, and how you can prevent it. Additionally, we’ll discuss how tools like Lightrun can enhance your application’s security by providing dynamic observability without the need for analyzing and remediating potential log injections in your code.
Understanding Log Injection
Log injection occurs when an attacker manipulates log entries to inject malicious content. This can lead to various security risks, including data breaches, unauthorized access, and even remote code execution. To understand log injection better, let’s look at a simple example:
# Example vulnerable Python code
user_input = request.get("user_input")
log.info("User entered: " + user_input)# Potential log injection by an attacker
malicious_input = '"; INFO: User logged out=attacker; --'
log.info("User entered: " + malicious_input)In this scenario, an attacker submits the input “; INFO: User logged out=attacker; — to manipulate the log entry. The resulting log entry would falsely indicate that a user logged out:
User entered: "; INFO: User logged out=attacker; --This illustrates how log injection can be used to craft deceptive log messages, posing a threat to the integrity and security of the application logs.
Risks of Log Injection
- Data exposure: Attackers can inject sensitive information into logs.
- Command injection: Log injection can lead to the execution of unintended commands.
- Possible Cross Site Scripting (XSS) attack – an attacker may attempt to inject malicious scripts into a web application, targeting users who access the application and potentially compromising their data or sessions.
- Injecting a virus string involves inserting malicious code into the log file with the intention of corrupting its content or compromising the system.
- Log Forging attack – A malicious user can compromise the integrity of application logs by creating a dummy log with events like the creation of a successful admin user or failed database connections, rendering the log file less meaningful; in scenarios where logs serve as monitoring data, injecting a payload to forge suspicious logs, such as repeatedly logging “user victim_user denied access for providing incorrect credentials,” could trigger email alarms or, at worst, result in the temporary blocking of the victim user.
- Denial Of Service attack (DOS) – Injecting a payload directly into the log file allows an attacker to log numerous lines of random strings, increasing the log file size and potentially causing server crashes due to memory space exhaustion, especially in cases where the log file and application share the same server, leading to a potential Denial of Service attack.
Best Practices for Preventing Log Injection
Sanitize user input
Always validate and sanitize user input before including it in log entries.
# Sanitized Python code
user_input = sanitize(request.get("user_input"))
log.info("User entered: " + user_input)Use parameterized logging
Most logging frameworks support parameterized logging, which automatically escapes special characters.
# Parameterized Python code
user_input = request.get("user_input")
log.info("User entered: %s", user_input)URL encoding
Encoding URLs can aid in reducing the risk of log injection vulnerabilities by transforming special characters in the input. This process complicates the task for attackers attempting to inject malicious code. Through URL encoding, special characters are replaced with percent-encoded representations, enhancing the difficulty for attackers to exploit the input and inject arbitrary log entries. Nevertheless, it is crucial to recognize that relying solely on URL encoding may not entirely eliminate the risk. Implementing additional security measures, such as input validation and proper sanitation, is essential.
Dynamic Observability with Lightrun
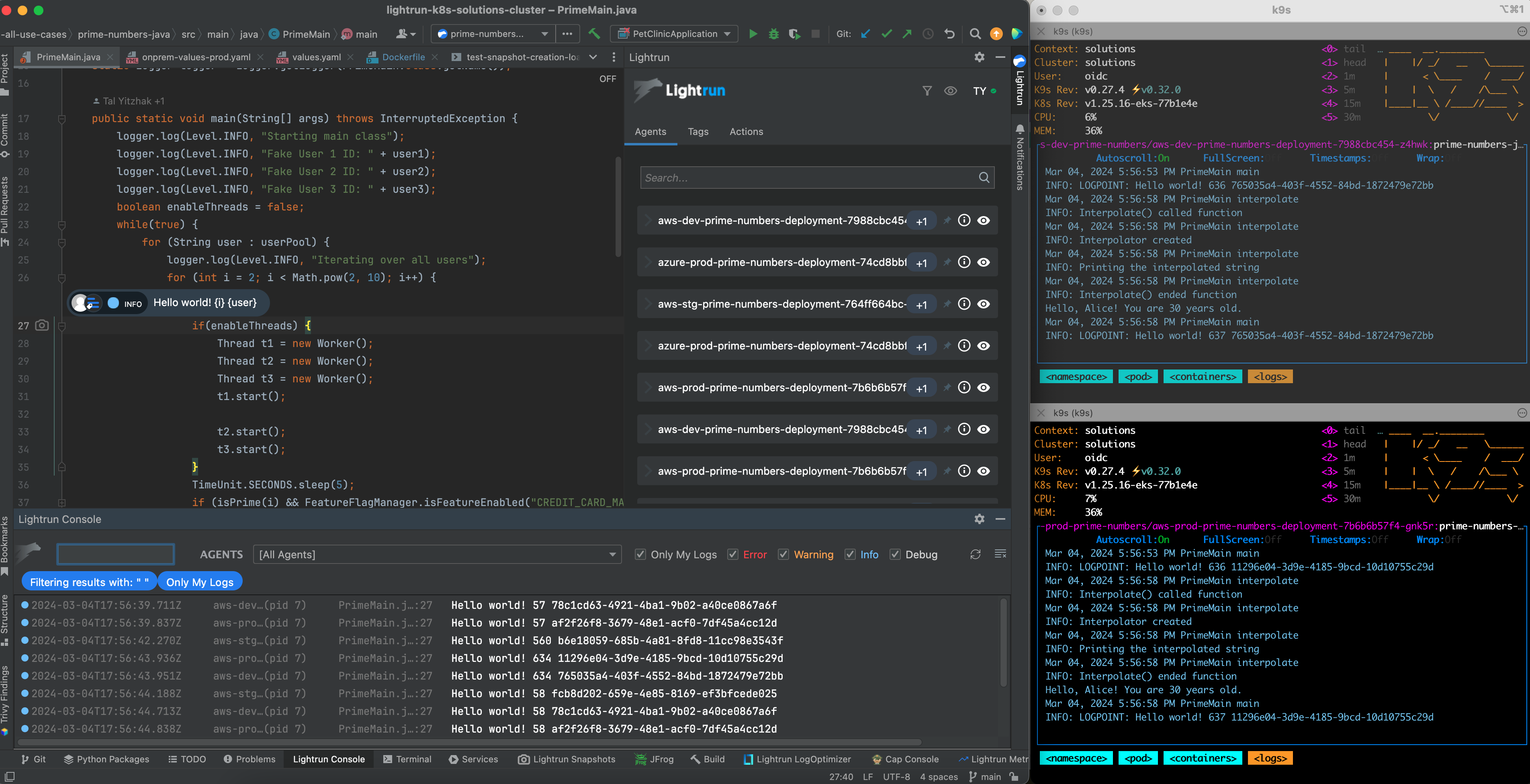
Lightrun is a dynamic observability tool that enables developers to instrument their code on the fly, allowing for real-time insights without the need for manual log injections. It enhances debugging and monitoring capabilities by providing a flexible and efficient way to add logs and collect data without modifying the source code.With Lightrun, developers can dynamically add logs in real-time without the need for manual injections, avoiding the inclusion of potentially vulnerable user-related data. This allows for on-the-fly instrumentation of code, enhancing observability without the risks associated with static log additions.
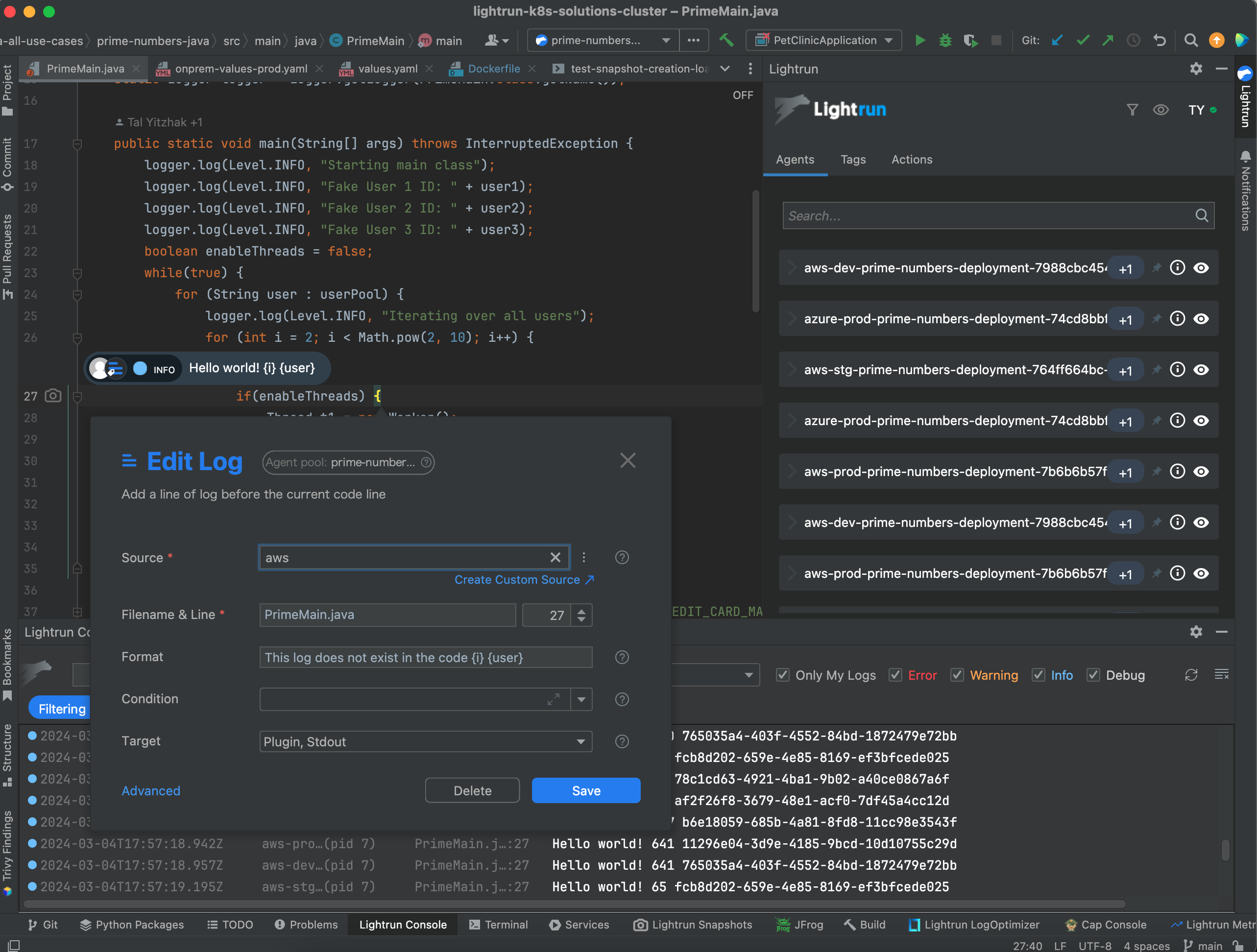
Adding a dynamic log using the Lightrun IDE Plugin for IntelliJ is very simple:
Source – Where would you like to add the log – based on specific agents/tags.
Format – This pertains to the log details; everything within {} represents the Java expression undergoing evaluation.
Condition – Developers can set specific terms for a log to be executed; Likely in the context of some user or transaction that occurs.
Target – Developers can specify where the log will be sent into. It can be either to the developer’s plugin ONLY or the standard output of the application.
Well, if Lightrun dynamically creates a log, how does Lightrun safeguard against log injection attacks?
- Lightrun’s patented Sandbox mechanism limits CPU usage and log frequency, preventing server crashes and potential DDoS attacks via log injection attacks.
- Dynamic logs can be sent exclusively to the developer’s IDE, avoiding appearance in customer APM tools and automatically expiring to manage log space efficiently.
- Sensitive data is safeguarded through lightrun’s PII Redaction capabilities on both the agent and server levels.
- Removing logs susceptible to injection risks from the code and creating them exclusively through Lightrun ensures controlled and secure log generation
It’s crucial to note that certain logs should be retained. Lightrun’s solution aims to mitigate risks without advocating for the complete removal of logs.
Conclusion
Given that log injection vulnerabilities present a considerable threat to application security, it is crucial for developers to follow best practices. By incorporating measures such as input validation, implementing parameterized logging, and utilizing tools like Lightrun, developers can substantially diminish the risk of log injection and thereby enhance the overall security of their applications.
Remember, proactive measures and a security-first mindset are essential to building robust and resilient applications.
It’s Really not that Complicated.
You can actually understand what’s going on inside your live applications.