
5 Tips to Improve How You Use Github Dependabot
Software development doesn’t end when deployment is complete. Instead, developers constantly tamper with the code even after deploying the app. Staying up-to-date with security fixes, bugs, and dependencies is crucial to ensure your app performs properly. After all, nobody wants a malfunctioning product, right?
GitHub Dependabotis one of the several tools you can use to update dependencies.
In this article, we show you several tips you can use to improve your GitHub Dependabot experience and unlock its maximum potential.
What is GitHub Dependabot?
GitHub Dependabot is a tool that helps developers keep dependencies up-to-date. At first, it was launched as an external service but was recently acquired and integrated natively into GitHub. Therefore, now it is a freely available tool for those who host their project repositories in GitHub.
GitHub Dependabot checks your dependencies regularly in search of outdated requirements within your repositories, as constant observability and monitoring are two essential methods in managing bugs and defects. It is an important and beneficial service you should consider using, as it helps you identify and fix vulnerable dependencies at the earliest stages.
How GitHub Dependabot works?
Dependabot configuration in a project is a straightforward process of adding a file by the name dependabot.yml under the .github/ directory. It contains critical configuration options such as the package ecosystem and schedule, telling Dependabot how to operate. This documentation includes a complete list of such configuration options with detailed information. Below is an example of what a simple dependabot.yml file looks like.
version: 2
updates:
– package-ecosystem: “npm”
directory: “/”
schedule:
interval: “weekly”
Dependabot automatically opens a pull request when a dependency in your repository runs out of date. In addition, it automates the dependency updates, includes compatibility scores to indicate whether it would cause breaking changes to the project by updating the dependency, and alerts about security flaws and vulnerabilities. GitHub Dependabot helps to keep your supply chain secure by monitoring the dependencies you include in your project.
Benefits of GitHub Dependabot
There are multiple advantages of enabling Dependabot in your project. Some of these advantages include:
- It ensures you are aware of the latest versions available for the dependencies you have used
- It is entirely free to use
- The configuration process is straightforward
- Ease in managing pull requests with a set of quick comment commands
- It provides you with a compatibility score to help you decide whether to merge the update to your project when enough information is available.
How to improve your use of GitHub Dependabot
Dependabot is a valuable asset for a developer to keep the dependency libraries automatically updated. The following tips will prove helpful in your journey with Dependabot to reap its maximum benefits.
1. Enabling Dependabot alerts and security updates
Dependabot alerts and security updates eliminate the hassle of identifying your dependencies’ security risks and maintenance requirements on your own. Once enabled, Dependabot alerts and Dependabot security updates identify vulnerabilities in your packages efficiently and send alerts.
In addition, you will receive an automatically generated pull request to update your dependency to the closest and safest version whenever Dependabot can suggest a fix.
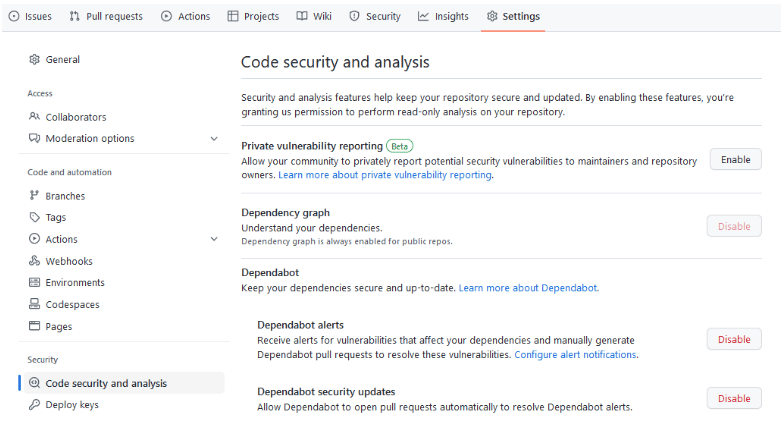
If you have not enabled this feature yet, follow the four simple steps below to activate it.
- Navigate to the Settings page of your repository.
- Select the Code Security & Analysis tab.
- Click ‘Enable’ for Dependabot alerts.
- Click ‘Enable’ for Dependabot security updates.
You can follow the same steps to check whether you have already enabled these two options.
2. Automating Dependabot merges
Even though Dependabot pull requests are critical, it can be cumbersome and time-consuming to review, approve, and merge them manually when working with many repositories. That is where Dependabot merge automation comes in.
You can use GitHub actions and GitHub CLI to automate these processes. It can contribute to improving your GitHub Dependabot experience, especially when it comes to working with multiple repositories. If you want to try this out, you can refer to the guides below to automate approving and merging Dependabot pull requests.
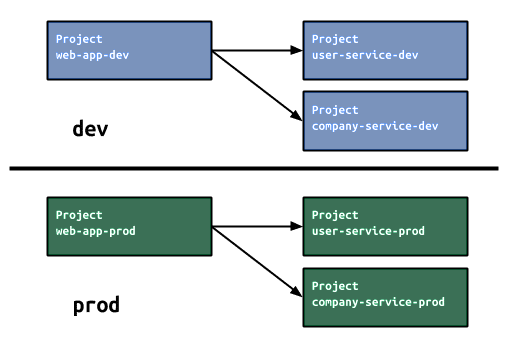
3. Separate development from production dependencies
When using GitHub Dependabot, it is important to distinguish between the development dependencies and production dependencies you use. In contrast to the development dependencies, most of the dependencies used in production are more likely to contain bugs and vulnerabilities.
The Dependabot alerts display a label in the UI to make it easier to distinguish whether the alert is related to production or development dependencies. That will help you assess the alerts more easily and prioritize them when handling vulnerabilities.
You can use Lightrun to improve your visibility and monitoring of logs, traces, and metrics and to detect and resolve vulnerabilities in the production stages. Plus, you can find the list of ecosystems where marking development dependencies is supported for Dependabot alerts here
4. Creating an organization secret for Dependabot
Going ahead of keeping your packages up-to-date, GitHub Dependabot is also capable of keeping Actions up-to-date in the GitHub Actions Workflow. Apart from the public marketplace actions, you can also use this feature on your organization’s custom actions.
By using a GitHub repository as a registry and a Dependabot secret, you can implement this for your custom actions. Here, you can create an organization secret and use a policy to limit the repositories that have access to the secret. It’s important to note that you must have admin access to create an organization secret. Here’s how you can do it:
- Navigate to your organization’s Settings page.
- Select Secrets from the Security tab and click on Dependabot.
- Click New organization secret and input a name and value.
- Select the access policy of your choice from the Repository access.
- If you selected Selected repositories, click the settings icon and choose the repositories you need.
You can read more about GitHub Dependabot for Actions by referring to this documentation.
5. Assessing health across your dependency tree
It is a best practice to check your dependency tree from time to time to assess the vulnerabilities and risks. When analyzing the dependency tree, you may encounter instances where a single dependency results in many alerts. It is best to find an alternative for that dependency in such cases.
Assessing health across your dependency tree will be handy as it shows how vulnerabilities are nested and linked. Sometimes you may be able to resolve multiple alerts with a single package version upgrade by looking at these links.
Monitoring your dependencies
Keeping the project you deliver up-to-date is an integral part of the developer’s duty. If ignored, out-of-date dependencies will make maintenance harder, take unnecessary time to fix, and cause the product to malfunction. Therefore, it is essential to monitor these dependencies regularly.
But worry not: Lightrun can help you. Our solution lets you gain visibility throughout your entire CD/CI pipeline by easily instrumenting and monitoring logs, traces, and metrics. You can get a free demo to experience how it works first-hand.
It’s Really not that Complicated.
You can actually understand what’s going on inside your live applications.